- ASIC
- Battery management ICs
- Clocks and timing solutions
- ESD and surge protection devices
- Automotive Ethernet
- Evaluation Boards
- High reliability
- Isolation
- Memories
- Microcontroller
- Power
- RF
- Security and smart card solutions
- Sensor technology
- Small signal transistors and diodes
- Transceivers
- Universal Serial Bus (USB)
- Wireless connectivity
- Search Tools
- Technology
- Packages
- Product Information
- Ordering
- Overview
- Automotive Ethernet Bridges
- Automotive Ethernet PHY for in-vehicle networking
- Automotive Ethernet Switches for in-vehicle networking
- Overview
- Defense
- High-reliability custom services
- NewSpace
- Space
- Overview
- Embedded flash IP solutions
- Flash+RAM MCP solutions
- F-RAM (Ferroelectric RAM)
- NOR flash
- nvSRAM (non-volatile SRAM)
- PSRAM (Pseudostatic RAM)
- Radiation hardened and high-reliability memories
- SRAM (static RAM)
- Wafer and die memory solutions
- Overview
- 32-bit FM Arm® Cortex® Microcontroller
- 32-bit AURIX™ TriCore™ microcontroller
- 32-bit PSOC™ Arm® Cortex® microcontroller
- 32-bit TRAVEO™ T2G Arm® Cortex® microcontroller
- 32-bit XMC™ industrial microcontroller Arm® Cortex®-M
- Legacy microcontroller
- Motor control SoCs/SiPs
- Sensing controllers
- Overview
- AC-DC power conversion
- Automotive conventional powertrain ICs
- Class D audio amplifier ICs
- Contactless power and sensing ICs
- DC-DC converters
- Diodes and thyristors (Si/SiC)
- Gallium nitride (GaN)
- Gate driver ICs
- IGBTs – Insulated gate bipolar transistors
- Intelligent power modules (IPM)
- LED driver ICs
- Motor drivers
- Power MOSFETs
- Power modules
- Power supply ICs
- Protection and monitoring ICs
- Silicon carbide (SiC)
- Smart power switches
- Solid state relays
- Wireless charging ICs
- Overview
- Antenna cross switches
- Antenna tuners
- Bias and control
- Coupler
- Driver amplifiers
- High Reliability Discrete
- Low noise amplifiers (LNAs)
- RF diode
- RF switches
- RF transistors
- Wireless control receiver
- Overview
- Calypso® products
- CIPURSE™ products
- Contactless memories
- OPTIGA™ embedded security solutions
- SECORA™ security solutions
- Security controllers
- Smart card modules
- Smart solutions for government ID
- Overview
- ToF 3D image sensors
- Current sensors
- Gas sensors
- Inductive position sensors
- MEMS microphones
- Pressure sensors
- Radar sensors
- Magnetic position sensors
- Magnetic speed sensors
- Overview
- Bipolar transistors
- Diodes
- Small signal/small power MOSFET
- Overview
- Automotive transceivers
- Control communication
- Powerline communications
- Overview
- USB 2.0 peripheral controllers
- USB 3.2 peripheral controllers
- USB hub controllers
- USB PD high-voltage microcontrollers
- USB-C AC-DC and DC-DC charging solutions
- USB-C charging port controllers
- USB-C Power Delivery controllers
- Overview
- AIROC™ Automotive wireless
- AIROC™ Bluetooth® and multiprotocol
- AIROC™ connected MCU
- AIROC™ Wi-Fi + Bluetooth® combos
- Overview
- Commercial off-the-shelf (COTs) memory portfolio
- Defense memory portfolio
- High-reliability power conversion and management
- Overview
- Rad hard microwave and RF
- Radiation hardened power
- Space memory portfolio
- Overview
- Parallel NOR flash
- SEMPER™ NOR flash family
- SEMPER™ X1 LPDDR flash
- Serial NOR flash
- Overview
- FM0+ 32-bit Arm® Cortex®-M0+ microcontroller (MCU) families
-
FM3 32-bit Arm® Cortex®-M3 microcontroller (MCU) families
- Overview
- FM3 CY9AFx1xK series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx1xL/M/N series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx2xK/L series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx3xK/L series ultra-low leak Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx4xL/M/N series low power Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx5xM/N/R series low power Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFxAxL/M/N series ultra-low leak Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx1xN/R high-performance series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx1xS/T high-performance series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx2xJ series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx2xK/L/M series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx2xS/T series Arm® Cortex®-M3 microcontroller (MCU)
-
FM4 32-bit Arm® Cortex®-M4 microcontroller (MCU) families
- Overview
- FM4 CY9BFx6xK/L high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- FM4 CY9BFx6xM/N/R high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- FM4 S6E2C high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- FM4 S6E2G series connectivity Arm® Cortex®-M4F microcontroller (MCU)
- FM4 S6E2H high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- Overview
-
32-bit TriCore™ AURIX™ – TC2x
- Overview
- AURIX™ family – TC21xL
- AURIX™ family – TC21xSC (wireless charging)
- AURIX™ family – TC22xL
- AURIX™ family – TC23xL
- AURIX™ family – TC23xLA (ADAS)
- AURIX™ family – TC23xLX
- AURIX™ family – TC264DA (ADAS)
- AURIX™ family – TC26xD
- AURIX™ family – TC27xT
- AURIX™ family – TC297TA (ADAS)
- AURIX™ family – TC29xT
- AURIX™ family – TC29xTT (ADAS)
- AURIX™ family – TC29xTX
- AURIX™ TC2x emulation devices
-
32-bit TriCore™ AURIX™ – TC3x
- Overview
- AURIX™ family - TC32xLP
- AURIX™ family – TC33xDA
- AURIX™ family - TC33xLP
- AURIX™ family – TC35xTA (ADAS)
- AURIX™ family – TC36xDP
- AURIX™ family – TC37xTP
- AURIX™ family – TC37xTX
- AURIX™ family – TC38xQP
- AURIX™ family – TC39xXA (ADAS)
- AURIX™ family – TC39xXX
- AURIX™ family – TC3Ex
- AURIX™ TC37xTE (emulation devices)
- AURIX™ TC39xXE (emulation devices)
- 32-bit TriCore™ AURIX™ – TC4x
- Overview
- PSOC™ 4 Arm® Cortex®-M0/M0+
- PSOC™ 4 HV Arm® Cortex®-M0+
- PSOC™ 5 LP Arm® Cortex®-M3
- PSOC™ 6 Arm® Cortex®-M4/M0+
- PSOC™ Multitouch Arm® Cortex®-M0
- PSOC™ Control Arm® Cortex®-M33
- PSOC™ Automotive 4: Arm® Cortex®-M0/M0+
- PSOC™ Edge Arm® Cortex® M55/M33
- Overview
- 32-bit TRAVEO™ T2G Arm® Cortex® for body
- 32-bit TRAVEO™ T2G Arm® Cortex® for cluster
- Overview
- 32-bit XMC1000 industrial microcontroller Arm® Cortex®-M0
- 32-bit XMC4000 industrial microcontroller Arm® Cortex®-M4
- XMC5000 Industrial Microcontroller Arm® Cortex®-M4F
- 32-bit XMC7000 Industrial Microcontroller Arm® Cortex®-M7
- Overview
- Legacy 32-bit MCU
- Legacy 8-bit/16-bit microcontroller
- Other legacy MCUs
- Overview
- AC-DC integrated power stage - CoolSET™
- AC-DC PWM-PFC controller
- Overview
- Bridge rectifiers & AC switches
- CoolSiC™ Schottky diodes
- Diode bare dies
- Silicon diodes
- Thyristor / Diode Power Modules
- Thyristor soft starter modules
- Thyristor/diode discs
- Overview
- Automotive gate driver ICs
- Isolated Gate Driver ICs
- Gate driver ICs for GaN HEMTs
- Level-Shift Gate Driver ICs
- Low-Side Drivers
- Transformer Driver ICs
- Overview
- AC-DC LED driver ICs
- Ballast IC
- DC-DC LED driver IC
- LED dimming interface IC
- Linear LED driver IC
- LITIX™ - Automotive LED Driver IC
- NFC wireless configuration IC with PWM output
- VCSEL driver
- Overview
- BLDC motor drivers
- BDC motor drivers
- Stepper & servo motor drivers
- Motor drivers with MCU
- Bridge drivers with MOSFETs
- Gate driver ICs
- Overview
- Automotive MOSFET
- Dual MOSFETs
- MOSFET (Si & SiC) Modules
- N-channel depletion mode MOSFET
- N-channel MOSFETs
- P-channel MOSFETs
- Silicon carbide CoolSiC™ MOSFETs
- Small signal/small power MOSFET
- Overview
- Automotive transceivers
- Linear Voltage Regulators for Automotive Applications
- OPTIREG™ PMIC
- OPTIREG™ switcher
- OPTIREG™ System Basis Chips (SBC)
- Overview
- eFuse
-
High-side switches
- Overview
- Classic PROFET™ 12V | Automotive smart high-side switch
- Classic PROFET™ 24V | Automotive smart high-side switch
- Power PROFET™ + 12/24/48V | Automotive smart high-side switch
- PROFET™ + 12V | Automotive smart high-side switch
- PROFET™ + 24V | Automotive smart high-side switch
- PROFET™ + 48V | Automotive smart high-side switch
- PROFET™ +2 12V | Automotive smart high-side switch
- PROFET™ Industrial | Smart high-side switch
- PROFET™ Wire Guard 12V | Automotive eFuse
- Low-side switches
- Multichannel SPI Switches & Controller
- Overview
- Radar sensors for automotive
- Radar sensors for IoT
- Overview
- EZ-USB™ CX3 MIPI CSI2 to USB 3.0 camera controller
- EZ-USB™ FX10 & FX5N USB 10Gbps peripheral controller
- EZ-USB™ FX20 USB 20 Gbps peripheral controller
- EZ-USB™ FX3 USB 5 Gbps peripheral controller
- EZ-USB™ FX3S USB 5 Gbps peripheral controller with storage interface
- EZ-USB™ FX5 USB 5 Gbps peripheral controller
- EZ-USB™ SD3 USB 5 Gbps storage controller
- EZ-USB™ SX3 FIFO to USB 5 Gbps peripheral controller
- Overview
- EZ-PD™ CCG3 USB type-C port controller PD
- EZ-PD™ CCG3PA USB-C and PD
- EZ-PD™ CCG3PA-NFET USB-C PD controller
- EZ-PD™ CCG7x consumer USB-C Power Delivery & DC-DC controller
- EZ-PD™ PAG1: power adapter generation 1
- EZ-PD™ PAG2: Power Adapter Generation 2
- EZ-PD™ PAG2-PD USB-C PD Controller
- Overview
- EZ-PD™ ACG1F one-port USB-C controller
- EZ-PD™ CCG2 USB Type-C port controller
- EZ-PD™ CCG3PA Automotive USB-C and Power Delivery controller
- EZ-PD™ CCG4 two-port USB-C and PD
- EZ-PD™ CCG5 dual-port and CCG5C single-port USB-C PD controllers
- EZ-PD™ CCG6 one-port USB-C & PD controller
- EZ-PD™ CCG6_CFP and EZ-PD™ CCG8_CFP Dual-Single-Port USB-C PD
- EZ-PD™ CCG6DF dual-port and CCG6SF single-port USB-C PD controllers
- EZ-PD™ CCG7D Automotive dual-port USB-C PD + DC-DC controller
- EZ-PD™ CCG7S Automotive single-port USB-C PD solution with a DC-DC controller + FETs
- EZ-PD™ CCG7SAF Automotive Single-port USB-C PD + DC-DC Controller + FETs
- EZ-PD™ CCG8 dual-single-port USB-C PD
- EZ-PD™ CMG1 USB-C EMCA controller
- EZ-PD™ CMG2 USB-C EMCA controller with EPR
- LATEST IN
- Aerospace and defense
- Automotive
- Consumer electronics
- Health and lifestyle
- Home appliances
- Industrial
- Information and Communication Technology
- Renewables
- Robotics
- Security solutions
- Smart home and building
- Solutions
- Overview
- Defense applications
- Space applications
- Overview
- 48 V systems for EVs & mild hybrids
- ADAS & autonomous driving
- Automotive body electronics & power distribution
- Automotive LED lighting systems
- Chassis control & safety
- Electric vehicle drivetrain system
- EV thermal management system
- Internal combustion drivetrain systems
- In-vehicle infotainment & HMI
- Light electric vehicle solutions
- Overview
- Power adapters and chargers
- Complete system solutions for smart TVs
- Mobile device and smartphone solutions
- Multicopters and drones
- Power tools
- Semiconductor solutions for home entertainment applications
- Smart conference systems
- Overview
- Adapters and chargers
- Asset Tracking
- Battery formation and testing
- Electric forklifts
- Battery energy storage (BESS)
- EV charging
- High voltage solid-state power distribution
- Industrial automation
- Industrial motor drives and controls
- Industrial robots system solutions for Industry 4.0
- LED lighting system design
- Light electric vehicle solutions
- Power tools
- Power transmission and distribution
- Traction
- Uninterruptible power supplies (UPS)
- Overview
- Data center and AI data center solutions
- Edge computing
- Telecommunications infrastructure
- Machine Learning Edge AI
- Overview
- Battery formation and testing
- EV charging
- Hydrogen
- Photovoltaic
- Wind power
- Solid-state circuit breaker
- Battery energy storage (BESS)
- Overview
- Device authentication and brand protection
- Embedded security for the Internet of Things (IoT)
- eSIM applications
- Government identification
- Mobile security
- Payment solutions
- Access control and ticketing
- Overview
- Domestic robots
- Heating ventilation and air conditioning (HVAC)
- Home and building automation
- PC accessories
- Semiconductor solutions for home entertainment applications
- Overview
- Battery management systems (BMS)
- Connectivity
- Human Machine Interface
- Machine Learning Edge AI
- Motor control
- Power conversion
- Security
- Sensor solutions
- System diagnostics and analytics
- Overview
- Automotive auxiliary systems
- Automotive gateway
- Automotive power distribution
- Body control modules (BCM)
- Comfort & convenience electronics
- Zonal DC-DC converter 48 V-12 V
- Zone control unit
- Overview
- Automotive animated LED lighting system
- Automotive LED front single light functions
- Automotive LED rear single light functions
- Full LED headlight system - multi-channel LED driver
- LED drivers (electric two- & three-wheelers)
- LED pixel light controller - supply & communication
- Static interior ambient LED light
- Overview
- Active suspension control
- Airbag system
- Automotive braking solutions
- Automotive steering solutions
- Chassis domain control
- Reversible seatbelt pretensioner
- Overview
-
Automotive BMS
- Overview
- Automotive battery cell monitoring & balancing
- Automotive battery control unit (BCU)
- Automotive battery isolated communication
- Automotive battery management system (BMS) - 12 V to 24 V
- Automotive battery management system (BMS) - 48 V
- Automotive battery management system (BMS) - high-voltage
- Automotive battery pack monitoring
- Automotive battery passport & event logging
- Automotive battery protection & disconnection
- Automotive current sensing & coulomb counting
- BMS (electric two- & three-wheelers)
- EV charging
- EV inverters
- EV power conversion & OBC
- FCEV powertrain system
- Overview
- Automatic transmission hydraulic system
- Belt starter generator 48 V – inverter ISG
- Diesel direct injection
- Double-clutch transmission electrical control
- Double-clutch transmission hydraulic control
- Gasoline direct injection
- Multi-port fuel injection
- Small 1-cylinder combustion engine solution
- Small engine starter kit
- Transfer case brushed DC
- Transfer case brushless DC (BLDC)
- Overview
- Automotive head unit
- Automotive USB-C power & data solution
- Automotive instrument cluster
- Automotive telematics control unit (TCU)
- Center information display (CID)
- High-performance cockpit controller
- In-cabin wireless charging
- Smart instrument cluster (electric two- & three-wheelers)
- Overview
- E-bike solutions
- Two- & three-wheeler solutions
- Overview
- Audio amplifier solutions
- Complete system solutions for smart TVs
- Distribution audio amplifier unit solutions
- Home theater installation speaker system solutions
- Party speaker solutions
- PoE audio amplifier unit solutions
- Portable speaker solutions
- Powered active speaker systems
- Remote control
- Smart speaker designs
- Soundbar solutions
- Overview
- Data center and AI data center solutions
- Digital input/output (I/O) modules
- DIN rail power supply solutions
- Home and building automation
- Industrial HMI Monitors and Panels
- Industrial motor drives and controls
- Industrial PC
- Industrial robots system solutions for Industry 4.0
- Machine vision
- Mobile robots (AGV, AMR)
- Programmable logic controller (PLC)
- Solid-state circuit breaker
- Uninterruptible power supplies (UPS)
- Overview
- 48 V intermediate bus converter (IBC)
- AI accelerator cards
- AMD server CPUs
- Ampere CPUs
- FPGAs in datacenter applications
- Intel server CPUs
- Networking and switch platforms
- Power path protection
- Power system reliability modeling
- RAID storage
- Server battery backup units (BBU)
- Server power supply
- SmartNIC cards
- Overview
- AC-DC power conversion for telecommunications infrastructure
- DC-DC power conversion for telecommunications infrastructure
- FPGA in wired and wireless telecommunications applications
- Satellite communications
- Power system reliability modeling
- RF front end components for telecommunications infrastructure
- Overview
-
AC-DC power conversion
- Overview
- AC-DC auxiliary power supplies
- AC-DC power conversion for telecommunications infrastructure
- Adapters and chargers
- Automotive LED lighting systems
- Complete system solutions for smart TVs
- Desktop power supplies
- EV charging
- Industrial power supplies
- PoE power sourcing equipment (PSE)
- Server power supply units (PSU)
- Uninterruptible power supplies (UPS)
- DC-DC power conversion
- Overview
- Power supply health monitoring
- LATEST IN
- Digital documentation
- Evaluation boards
- Finder & selection tools
- Platforms
- Services
- Simulation & Modeling
- Software
- Tools
- Partners
- Infineon for Makers
- University Alliance Program
- Overview
- Bipolar Discs Finder
- Bipolar Module Finder
- Connected Secure Systems Finder
- Diode Rectifier Finder
- ESD Protection Finder
- Evaluation Board Finder
- Gate Driver Finder
- IGBT Discrete Finder
- IGBT Module Finder
- IPM Finder
- Microcontroller Finder
- MOSFET Finder
- PMIC Finder
- Product Finder
- PSOC™ and FMx MCU Board & Kit Finder
- Radar Finder
- Reference Design Finder
- Simulation Model Finder
- Smart Power Switch Finder
- Transceiver Finder
- Voltage Regulator Finder
- Wireless Connectivity Board & Kit Finder
- Overview
- AIROC™ software & tools
- AURIX™ software & tools
- DRIVECORE for automotive software development
- iMOTION™ software & tools
- Infineon Smart Power Switches & Gate Driver Tool Suite
- MOTIX™ software & tools
- OPTIGA™ software & tools
- PSOC™ software & tools
- TRAVEO™ software & tools
- XENSIV™ software & tools
- XMC™ software & tools
- Overview
- CoolGaN™ Simulation Tool (PLECS)
- HiRel Fit Rate Tool
- Infineon Designer
- Interactive product sheet
- IPOSIM Online Power Simulation Platform
- InfineonSpice Offline Simulation Tool
- OPTIREG™ automotive power supply ICs Simulation Tool (PLECS)
- Power MOSFET Simulation Models
- PowerEsim Switch Mode Power Supply Design Tool
- Solution Finder
- XENSIV™ Magnetic Sensor Simulation Tool
- Overview
- AURIX™ certifications
- AURIX™ development tools
-
AURIX™ Embedded Software
- Overview
- AURIX™ Applications software
- AURIX™ Artificial Intelligence
- AURIX™ Gateway
- AURIX™ iLLD Drivers
- Infineon safety
- AURIX™ Security
- AURIX™ TC3xx Motor Control Application Kit
- AURIX™ TC4x SW application architecture
- Infineon AUTOSAR
- Communication and Connectivity
- Middleware
- Non AUTOSAR OS/RTOS
- OTA
- AURIX™ Microcontroller Kits
- Overview
- TRAVEO™ Development Tools
- TRAVEO™ Embedded Software
- Overview
- XENSIV™ Development Tools
- XENSIV™ Embedded Software
- XENSIV™ evaluation boards
- Overview
- CAPSENSE™ Controllers Code Examples
- Memories for Embedded Systems Code Examples
- PSOC™ 1 Code Examples for PSOC™ Designer
- PSOC™ 3 Code Examples for PSOC™ Creator
- PSOC™ 3/4/5 Code Examples
- PSOC™ 4 Code Examples for PSOC™ Creator
- PSOC™ 6 Code Examples for PSOC™ Creator
- PSOC™ 63 Code Examples
- USB Controllers Code Examples
- Overview
- DEEPCRAFT™ AI Hub
- DEEPCRAFT™ Audio Enhancement
- DEEPCRAFT™ Model Converter
-
DEEPCRAFT™ Ready Models
- Overview
- DEEPCRAFT™ Ready Model for Baby Cry Detection
- DEEPCRAFT™ Ready Model for Cough Detection
- DEEPCRAFT™ Ready Model for Direction of Arrival (Sound)
- DEEPCRAFT™ Ready Model for Factory Alarm Detection
- DEEPCRAFT™ Ready Model for Fall Detection
- DEEPCRAFT™ Ready Model for Gesture Classification
- DEEPCRAFT™ Ready Model for Siren Detection
- DEEPCRAFT™ Ready Model for Snore Detection
- DEEPCRAFT™ Studio
- DEEPCRAFT™ Voice Assistant
- Overview
- AIROC™ Wi-Fi & Bluetooth EZ-Serial Module Firmware Platform
- AIROC™ Wi-Fi & Bluetooth Linux and Android Drivers
- emWin Graphics Library and GUI for PSOC™
- Infineon Complex Device Driver for Battery Management Systems
- Memory Solutions Hub
- PSOC™ 6 Peripheral Driver Library (PDL) for PSOC™ Creator
- USB Controllers EZ-USB™ GX3 Software and Drivers
- Overview
- CAPSENSE™ Controllers Configuration Tools EZ-Click
- DC-DC Integrated POL Voltage Regulators Configuration Tool – PowIRCenter
- EZ-USB™ SX3 Configuration Utility
- FM+ Configuration Tools
- FMx Configuration Tools
- Tranceiver IC Configuration Tool
- USB EZ-PD™ Configuration Utility
- USB EZ-PD™ Dock Configuration Utility
- USB EZ-USB™ HX3C Blaster Plus Configuration Utility
- USB UART Config Utility
- XENSIV™ Tire Pressure Sensor Programming
- Overview
- EZ-PD™ CCGx Dock Software Development Kit
-
FMx Softune IDE
- Overview
- RealOS™ Real-Time Operating System
- Softune IDE Language tools
- Softune Workbench
- Tool Lineup for F2MC-16 Family SOFTUNE V3
- Tool Lineup for F2MC-8FX Family SOFTUNE V3
- Tool Lineup for FR Family SOFTUNE V6
- Virtual Starter Kit
- Windows 10 operation of released SOFTUNE product
- Windows 7 operation of released SOFTUNE product
- Windows 8 operation of released SOFTUNE product
- ModusToolbox™ Software
- PSOC™ Creator Software
- Radar Development Kit
- RUST
- USB Controllers SDK
- Wireless Connectivity Bluetooth Mesh Helper Applications
- XMC™ DAVE™ Software
- Overview
- AIROC™ Bluetooth® Connect App Archive
- Cypress™ Programmer Archive
- EZ-PD™ CCGx Power Software Development Kit Archive
- ModusToolbox™ Software Archive
- PSOC™ Creator Archive
- PSOC™ Designer Archive
- PSOC™ Programmer Archive
- USB EZ-PD™ Configuration Utility Archives
- USB EZ-PD™ Host SDK Archives
- USB EZ-USB™ FX3 Archive
- USB EZ-USB™ HX3PD Configuration Utility Archive
- WICED™ Smart SDK Archive
- WICED™ Studio Archive
- Overview
- Infineon Developer Center Launcher
- Infineon Register Viewer
- Pin and Code Wizard
- Timing Solutions
- Wireless Connectivity
- LATEST IN
- Support
- Training
- Developer Community
- News
Business & Financial Press
Feb 16, 2026
Business & Financial Press
Feb 10, 2026
Business & Financial Press
Feb 04, 2026
Quarterly Report
Feb 04, 2026
- Company
- Our stories
- Events
- Press
- Investor
- Careers
- Quality
- Latest news
Business & Financial Press
Feb 16, 2026
Business & Financial Press
Feb 10, 2026
Business & Financial Press
Feb 04, 2026
Quarterly Report
Feb 04, 2026
Quantum computers use the law of quantum physics to process data at speeds far beyond what today‘s computers can achieve. While this brings tremendous opportunities, it also poses a significant risk: one day, quantum computing could break the public key cryptography algorithms (RSA, ECDSA) that secure online transactions today. To address this challenge, Infineon is at the forefront of research and standardization, collaborating with the academic community, industry partners, and government agencies to deve-lop and promote post-quantum cryptography (PQC) standards.
In 2024, Infineon made a huge step toward a quantum resistant world. We received the world’s first Common Criteria EAL6+ certification for a security controller comprising the secured implementation of a post-quantum cryptography (PQC) algorithm.
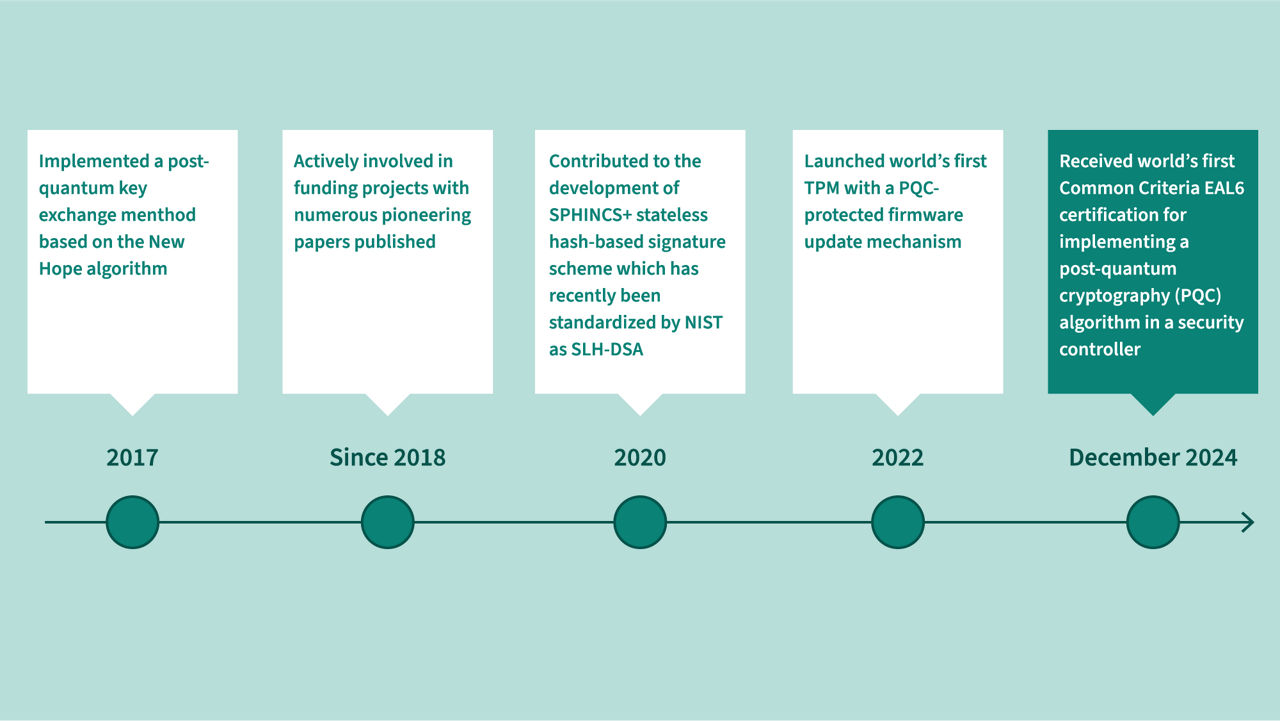


In addition, from 2025 on, Infineon PSOC™ microcontrollers (MCUs) are compliant with PQC requirements for firmware verification outlined in the Commercial National Security Algorithm (CNSA) Suite 2.0, easing companies’ transition to increased security in the quantum era.
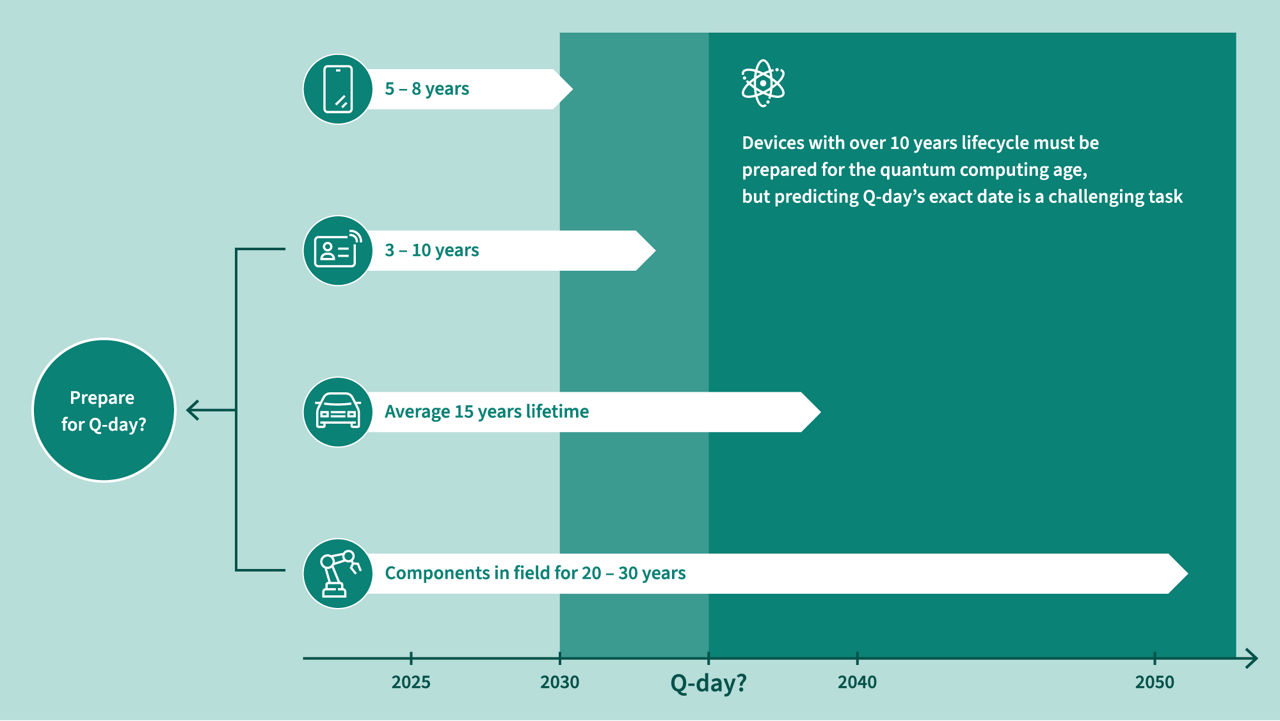
A particular concern is the „Harvest-Now-Decrypt-Later“ scenario, where adversaries store encrypted data for decryption once a powerful enough quantum computer becomes available—potentially as early as 2030-2035. This emerging reality makes post-quantum cryptography (PQC) essential for protecting long-term digital assets across finance, government, and healthcare sectors. Industries already understand the urgency of post-quantum cryptography so they can protect their assets beyond the next decade.
More information here











The migration to post-quantum security requires a strong consensus on the deployed algorithms and a high level of trust in their security. After an almost decade-long public evaluation and selection process, the US National Institute of Stan-dards and Technology (NIST) published in 2024 the first standards for quantum cryptography. By standardizing one key encapsulation algorithm (ML-KEM), two general-purpose signature schemes (ML-DSA, SLH-DSA) as well as two special-purpose signature schemes (XMSS, LMS), important cryptographic services within public key infrastructure can now be realized in a quantum-secured way.



PQC algorithms require more resources, such as memory, than traditional public key cryptography. Additionally, the key and signature sizes of PQC algorithms are significantly larger, which can impact data transfer time. For example, the key sizes for PQC algorithms can be several kilobytes, compared to the few hundred bits required for traditional elliptic curve cryptography. This can be a challenge for constrained devices and can lead to higher bandwidth requirements and increa-sed latency to the point where it renders the device useless.
Infineon’s approach to overcoming the PQC computational challenge
We have implemented a flexible hardware accelerator with side-channel protection and increased the RAM size of our products. This allows for more efficient processing of PQC algorithms, reducing the computational overhead and enabling faster execution times without compromising security. Our products are designed to support the efficient implementation of PQC schemes such as LMS/XMSS, ML-KEM (Kyber) and ML-DSA (Dilithium), which have been standardized according to NIST. By providing optimized hardware and software solutions, we are helping to mitigate the computational intensity of PQC schemes and are thus enabling the widespread adoption of PQC.
Implementing PQC in a secured way is still a highly challenging task. While PQC algorithms are mathematically designed to withstand attacks from quantum computers, their complex structure and larger key sizes make them vulnerable to fault- and side-channel attacks during operation. While traditional cryptography has benefited from decades of harden-ing against these attacks, PQC is a relatively young research area. Implementing PQC in a secured way requires deep un-derstanding of the underlying math as well as expertise in secured implementation technique.
How Infineon tackles the PQC implementation challenge
Infineon offers TEGRION with Integrity Guard 32 and side-channel protected hardware accelerator to enable efficient and secured implementations. In 2025, we become world‘s first company to receive Common Criteria EAL6, an industry- leading level of certification, for the secured implementation of a post-quantum cryptography algorithm on our TEGRION security controller.






Post-quantum security solutions are not simple drop-in replacements for existing protocols. Changes in protocols and a transition period with e.g. hybrid schemes (combining classical cryptography and PQC, as well as shipping products al-ready today with the possibility of in-field updates) are necessary for a smooth transition. This means that organizations will need to invest time and resources into updating their protocols and systems to support PQC, which can be a complex and time-consuming process.
Infineon’s advancements help tackle transition challenge
We already provide a flexible hardware platform and software building blocks to enable hybrid schemes and in-field up-dates. Additionally, our team brings expertise and competence in implementing quantum cryptography, further enhan-cing our capabilities.



PQC algorithms require more resources, such as memory, than traditional public key cryptography. Additionally, the key and signature sizes of PQC algorithms are significantly larger, which can impact data transfer time. For example, the key sizes for PQC algorithms can be several kilobytes, compared to the few hundred bits required for traditional elliptic curve cryptography. This can be a challenge for constrained devices and can lead to higher bandwidth requirements and increa-sed latency to the point where it renders the device useless.
Infineon’s approach to overcoming the PQC computational challenge
We have implemented a flexible hardware accelerator with side-channel protection and increased the RAM size of our products. This allows for more efficient processing of PQC algorithms, reducing the computational overhead and enabling faster execution times without compromising security. Our products are designed to support the efficient implementation of PQC schemes such as LMS/XMSS, ML-KEM (Kyber) and ML-DSA (Dilithium), which have been standardized according to NIST. By providing optimized hardware and software solutions, we are helping to mitigate the computational intensity of PQC schemes and are thus enabling the widespread adoption of PQC.
Implementing PQC in a secured way is still a highly challenging task. While PQC algorithms are mathematically designed to withstand attacks from quantum computers, their complex structure and larger key sizes make them vulnerable to fault- and side-channel attacks during operation. While traditional cryptography has benefited from decades of harden-ing against these attacks, PQC is a relatively young research area. Implementing PQC in a secured way requires deep un-derstanding of the underlying math as well as expertise in secured implementation technique.
How Infineon tackles the PQC implementation challenge
Infineon offers TEGRION with Integrity Guard 32 and side-channel protected hardware accelerator to enable efficient and secured implementations. In 2025, we become world‘s first company to receive Common Criteria EAL6, an industry- leading level of certification, for the secured implementation of a post-quantum cryptography algorithm on our TEGRION security controller.






Post-quantum security solutions are not simple drop-in replacements for existing protocols. Changes in protocols and a transition period with e.g. hybrid schemes (combining classical cryptography and PQC, as well as shipping products al-ready today with the possibility of in-field updates) are necessary for a smooth transition. This means that organizations will need to invest time and resources into updating their protocols and systems to support PQC, which can be a complex and time-consuming process.
Infineon’s advancements help tackle transition challenge
We already provide a flexible hardware platform and software building blocks to enable hybrid schemes and in-field up-dates. Additionally, our team brings expertise and competence in implementing quantum cryptography, further enhan-cing our capabilities.
With a series of breakthroughs in the field of PQC, Infineon enables customers to address today‘s PQC challenges. Our PQC-ready platforms provide a clear migration path toward a quantum-resilient future. As the first company to receive a Common Criteria EAL6 for the implementation of PQC on a security controller and the first to offer a PQC solution with a TPM as well as hardware products with specific support for PQC, we are well positioned to support you in future-proofing your assets.
To accelerate your time-to-market, we offer software that is already PQC-certified. This allows our customers to offer PQC-compliant and secured products and applications while continuing to focus on their core business. In addition, our hardware offering with the latest technologies such as our unique Integrity Guard 32 hardware security architecture enables a smooth hardware certification process with a short evaluation time.
