- ASIC
- Battery management ICs
- Clocks and timing solutions
- ESD and surge protection devices
- Automotive Ethernet
- Evaluation Boards
- High reliability
- Isolation
- Memories
- Microcontroller
- Power
- RF
- Security and smart card solutions
- Sensor technology
- Small signal transistors and diodes
- Transceivers
- Universal Serial Bus (USB)
- Wireless connectivity
- Search Tools
- Technology
- Packages
- Product Information
- Ordering
- Overview
- Automotive Ethernet Bridges
- Automotive Ethernet PHY for in-vehicle networking
- Automotive Ethernet Switches for in-vehicle networking
- Overview
- Defense
- High-reliability custom services
- NewSpace
- Space
- Overview
- Embedded flash IP solutions
- Flash+RAM MCP solutions
- F-RAM (Ferroelectric RAM)
- NOR flash
- nvSRAM (non-volatile SRAM)
- PSRAM (Pseudostatic RAM)
- Radiation hardened and high-reliability memories
- SRAM (static RAM)
- Wafer and die memory solutions
- Overview
- 32-bit FM Arm® Cortex® Microcontroller
- 32-bit AURIX™ TriCore™ microcontroller
- 32-bit PSOC™ Arm® Cortex® microcontroller
- 32-bit TRAVEO™ T2G Arm® Cortex® microcontroller
- 32-bit XMC™ industrial microcontroller Arm® Cortex®-M
- Legacy microcontroller
- MOTIX™ MCU | 32-bit motor control SoC based on Arm® Cortex®-M
- Sensing controllers
- Overview
- AC-DC power conversion
- Automotive conventional powertrain ICs
- Class D audio amplifier ICs
- Contactless power and sensing ICs
- DC-DC converters
- Diodes and thyristors (Si/SiC)
- Gallium nitride (GaN)
- Gate driver ICs
- IGBTs – Insulated gate bipolar transistors
- Intelligent power modules (IPM)
- LED driver ICs
- Motor control ICs
- Power MOSFETs
- Power modules
- Power supply ICs
- Protection and monitoring ICs
- Silicon carbide (SiC)
- Smart power switches
- Solid state relays
- Wireless charging ICs
- Overview
- Antenna cross switches
- Antenna tuners
- Bias and control
- Coupler
- Driver amplifiers
- High Reliability Discrete
- Low noise amplifiers (LNAs)
- RF diode
- RF switches
- RF transistors
- Wireless control receiver
- Overview
- Calypso® products
- CIPURSE™ products
- Contactless memories
- OPTIGA™ embedded security solutions
- SECORA™ security solutions
- Security controllers
- Smart card modules
- Smart solutions for government ID
- Overview
- ToF 3D image sensors
- Current sensors
- Gas sensors
- Inductive position sensors
- MEMS microphones
- Pressure sensors
- Radar sensors
- Magnetic position sensors
- Magnetic speed sensors
- Overview
- Bipolar transistors
- Diodes
- Small signal/small power MOSFET
- Overview
- Automotive transceivers
- Control communication
- Powerline communications
- Overview
- USB 2.0 peripheral controllers
- USB 3.2 peripheral controllers
- USB hub controllers
- USB PD high-voltage microcontrollers
- USB-C AC-DC and DC-DC charging solutions
- USB-C charging port controllers
- USB-C Power Delivery controllers
- Overview
- AIROC™ Automotive wireless
- AIROC™ Bluetooth® and multiprotocol
- AIROC™ connected MCU
- AIROC™ Wi-Fi + Bluetooth® combos
- Overview
- Commercial off-the-shelf (COTs) memory portfolio
- Defense memory portfolio
- High-reliability power conversion and management
- Overview
- Rad hard microwave and RF
- Radiation hardened power
- Space memory portfolio
- Overview
- Parallel NOR flash
- SEMPER™ NOR flash family
- SEMPER™ X1 LPDDR flash
- Serial NOR flash
- Overview
- FM0+ 32-bit Arm® Cortex®-M0+ microcontroller (MCU) families
-
FM3 32-bit Arm® Cortex®-M3 microcontroller (MCU) families
- Overview
- FM3 CY9AFx1xK series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx1xL/M/N series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx2xK/L series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx3xK/L series ultra-low leak Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx4xL/M/N series low power Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx5xM/N/R series low power Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFxAxL/M/N series ultra-low leak Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx1xN/R high-performance series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx1xS/T high-performance series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx2xJ series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx2xK/L/M series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx2xS/T series Arm® Cortex®-M3 microcontroller (MCU)
-
FM4 32-bit Arm® Cortex®-M4 microcontroller (MCU) families
- Overview
- FM4 CY9BFx6xK/L high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- FM4 CY9BFx6xM/N/R high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- FM4 S6E2C high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- FM4 S6E2G series connectivity Arm® Cortex®-M4F microcontroller (MCU)
- FM4 S6E2H high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- Overview
-
32-bit TriCore™ AURIX™ – TC2x
- Overview
- AURIX™ family – TC21xL
- AURIX™ family – TC21xSC (wireless charging)
- AURIX™ family – TC22xL
- AURIX™ family – TC23xL
- AURIX™ family – TC23xLA (ADAS)
- AURIX™ family – TC23xLX
- AURIX™ family – TC264DA (ADAS)
- AURIX™ family – TC26xD
- AURIX™ family – TC27xT
- AURIX™ family – TC297TA (ADAS)
- AURIX™ family – TC29xT
- AURIX™ family – TC29xTT (ADAS)
- AURIX™ family – TC29xTX
- AURIX™ TC2x emulation devices
-
32-bit TriCore™ AURIX™ – TC3x
- Overview
- AURIX™ family - TC32xLP
- AURIX™ family – TC33xDA
- AURIX™ family - TC33xLP
- AURIX™ family – TC35xTA (ADAS)
- AURIX™ family – TC36xDP
- AURIX™ family – TC37xTP
- AURIX™ family – TC37xTX
- AURIX™ family – TC38xQP
- AURIX™ family – TC39xXA (ADAS)
- AURIX™ family – TC39xXX
- AURIX™ family – TC3Ex
- AURIX™ TC37xTE (emulation devices)
- AURIX™ TC39xXE (emulation devices)
- 32-bit TriCore™ AURIX™ – TC4x
- Overview
- PSOC™ 4 Arm® Cortex®-M0/M0+
- PSOC™ 4 HV Arm® Cortex®-M0+
- PSOC™ 5 LP Arm® Cortex®-M3
- PSOC™ 6 Arm® Cortex®-M4/M0+
- PSOC™ Multitouch Arm® Cortex®-M0
- PSOC™ Control Arm® Cortex®-M33
- PSOC™ Automotive 4: Arm® Cortex®-M0/M0+
- PSOC™ Edge Arm® Cortex® M55/M33
- Overview
- 32-bit TRAVEO™ T2G Arm® Cortex® for body
- 32-bit TRAVEO™ T2G Arm® Cortex® for cluster
- Overview
- 32-bit XMC1000 industrial microcontroller Arm® Cortex®-M0
- 32-bit XMC4000 industrial microcontroller Arm® Cortex®-M4
- XMC5000 Industrial Microcontroller Arm® Cortex®-M4F
- 32-bit XMC7000 Industrial Microcontroller Arm® Cortex®-M7
- Overview
- Legacy 32-bit MCU
- Legacy 8-bit/16-bit microcontroller
- Other legacy MCUs
- Overview
- AC-DC integrated power stage - CoolSET™
- AC-DC PWM-PFC controller
- Overview
- Bridge rectifiers & AC switches
- CoolSiC™ Schottky diodes
- Diode bare dies
- Silicon diodes
- Thyristor / Diode Power Modules
- Thyristor soft starter modules
- Thyristor/diode discs
- Overview
- Automotive gate driver ICs
- Isolated Gate Driver ICs
- Gate driver ICs for GaN HEMTs
- Level-Shift Gate Driver ICs
- Low-Side Drivers
- Transformer Driver ICs
- Overview
- AC-DC LED driver ICs
- Ballast IC
- DC-DC LED driver IC
- LED dimming interface IC
- Linear LED driver IC
- LITIX™ - Automotive LED Driver IC
- NFC wireless configuration IC with PWM output
- VCSEL driver
- Overview
- 32-bit PSOC™ Control Arm® Cortex®-M33 MCU
- iMOTION™ Integrated motor control solutions
- MOTIX™ MCU | 32-bit motor control SoC based on Arm® Cortex®-M
- MOTIX™ motor control ICs for BLDC motors
- MOTIX™ motor control ICs for brushed DC motors
- MOTIX™ multi half-bridge ICs for servo and stepper motors
- Overview
- Automotive MOSFET
- Dual MOSFETs
- MOSFET (Si & SiC) Modules
- N-channel depletion mode MOSFET
- N-channel MOSFETs
- P-channel MOSFETs
- Silicon carbide CoolSiC™ MOSFETs
- Small signal/small power MOSFET
- Overview
- Automotive transceivers
- Linear Voltage Regulators for Automotive Applications
- OPTIREG™ PMIC
- OPTIREG™ switcher
- OPTIREG™ System Basis Chips (SBC)
- Overview
- eFuse
-
High-side switches
- Overview
- Classic PROFET™ 12V | Automotive smart high-side switch
- Classic PROFET™ 24V | Automotive smart high-side switch
- Power PROFET™ + 12/24/48V | Automotive smart high-side switch
- PROFET™ + 12V | Automotive smart high-side switch
- PROFET™ + 24V | Automotive smart high-side switch
- PROFET™ + 48V | Automotive smart high-side switch
- PROFET™ +2 12V | Automotive smart high-side switch
- PROFET™ Industrial | Smart high-side switch
- PROFET™ Wire Guard 12V | Automotive eFuse
- Low-side switches
- Multichannel SPI Switches & Controller
- Overview
- Radar sensors for automotive
- Radar sensors for IoT
- Overview
- EZ-USB™ CX3 MIPI CSI2 to USB 3.0 camera controller
- EZ-USB™ FX10 & FX5N USB 10Gbps peripheral controller
- EZ-USB™ FX20 USB 20 Gbps peripheral controller
- EZ-USB™ FX3 USB 5 Gbps peripheral controller
- EZ-USB™ FX3S USB 5 Gbps peripheral controller with storage interface
- EZ-USB™ FX5 USB 5 Gbps peripheral controller
- EZ-USB™ SD3 USB 5 Gbps storage controller
- EZ-USB™ SX3 FIFO to USB 5 Gbps peripheral controller
- Overview
- EZ-PD™ CCG3 USB type-C port controller PD
- EZ-PD™ CCG3PA USB-C and PD
- EZ-PD™ CCG3PA-NFET USB-C PD controller
- EZ-PD™ CCG7x consumer USB-C Power Delivery & DC-DC controller
- EZ-PD™ PAG1: power adapter generation 1
- EZ-PD™ PAG2: Power Adapter Generation 2
- EZ-PD™ PAG2-PD USB-C PD Controller
- Overview
- EZ-PD™ ACG1F one-port USB-C controller
- EZ-PD™ CCG2 USB Type-C port controller
- EZ-PD™ CCG3PA Automotive USB-C and Power Delivery controller
- EZ-PD™ CCG4 two-port USB-C and PD
- EZ-PD™ CCG5 dual-port and CCG5C single-port USB-C PD controllers
- EZ-PD™ CCG6 one-port USB-C & PD controller
- EZ-PD™ CCG6_CFP and EZ-PD™ CCG8_CFP Dual-Single-Port USB-C PD
- EZ-PD™ CCG6DF dual-port and CCG6SF single-port USB-C PD controllers
- EZ-PD™ CCG7D Automotive dual-port USB-C PD + DC-DC controller
- EZ-PD™ CCG7S Automotive single-port USB-C PD solution with a DC-DC controller
- EZ-PD™ CCG7SAF Automotive Single-port USB-C PD + DC-DC Controller + FETs
- EZ-PD™ CCG8 dual-single-port USB-C PD
- EZ-PD™ CMG1 USB-C EMCA controller
- EZ-PD™ CMG2 USB-C EMCA controller with EPR
- LATEST IN
- Aerospace and defense
- Automotive
- Consumer electronics
- Health and lifestyle
- Home appliances
- Industrial
- Information and Communication Technology
- Renewables
- Robotics
- Security solutions
- Smart home and building
- Solutions
- Overview
- Defense applications
- Space applications
- Overview
- 48 V systems for EVs & mild hybrids
- ADAS & autonomous driving
- Automotive body electronics & power distribution
- Automotive LED lighting systems
- Chassis control & safety
- Electric vehicle drivetrain system
- EV thermal management system
- Internal combustion drivetrain systems
- In-vehicle infotainment & HMI
- Light electric vehicle solutions
- Overview
- Power adapters and chargers
- Complete system solutions for smart TVs
- Mobile device and smartphone solutions
- Multicopters and drones
- Power tools
- Semiconductor solutions for home entertainment applications
- Smart conference systems
- Overview
- Adapters and chargers
- Asset Tracking
- Battery formation and testing
- Electric forklifts
- Battery energy storage (BESS)
- EV charging
- High voltage solid-state power distribution
- Industrial automation
- Industrial motor drives and controls
- Industrial robots system solutions for Industry 4.0
- LED lighting system design
- Light electric vehicle solutions
- Power tools
- Power transmission and distribution
- Traction
- Uninterruptible power supplies (UPS)
- Overview
- Data center and AI data center solutions
- Edge computing
- Telecommunications infrastructure
- Machine Learning Edge AI
- Overview
- Battery formation and testing
- EV charging
- Hydrogen
- Photovoltaic
- Wind power
- Solid-state circuit breaker
- Battery energy storage (BESS)
- Overview
- Device authentication and brand protection
- Embedded security for the Internet of Things (IoT)
- eSIM applications
- Government identification
- Mobile security
- Payment solutions
- Access control and ticketing
- Overview
- Domestic robots
- Heating ventilation and air conditioning (HVAC)
- Home and building automation
- PC accessories
- Semiconductor solutions for home entertainment applications
- Overview
- Battery management systems (BMS)
- Connectivity
- Human Machine Interface
- Machine Learning Edge AI
- Motor control
- Power conversion
- Security
- Sensor solutions
- System diagnostics and analytics
- Overview
- Automotive auxiliary systems
- Automotive gateway
- Automotive power distribution
- Body control modules (BCM)
- Comfort & convenience electronics
- Zonal DC-DC converter 48 V-12 V
- Zone control unit
- Overview
- Automotive animated LED lighting system
- Automotive LED front single light functions
- Automotive LED rear single light functions
- Full LED headlight system - multi-channel LED driver
- LED drivers (electric two- & three-wheelers)
- LED pixel light controller - supply & communication
- Static interior ambient LED light
- Overview
- Active suspension control
- Airbag system
- Automotive braking solutions
- Automotive steering solutions
- Chassis domain control
- Reversible seatbelt pretensioner
- Overview
-
Automotive BMS
- Overview
- Automotive battery cell monitoring & balancing
- Automotive battery control unit (BCU)
- Automotive battery isolated communication
- Automotive battery management system (BMS) - 12 V to 24 V
- Automotive battery management system (BMS) - 48 V
- Automotive battery management system (BMS) - high-voltage
- Automotive battery pack monitoring
- Automotive battery passport & event logging
- Automotive battery protection & disconnection
- Automotive current sensing & coulomb counting
- BMS (electric two- & three-wheelers)
- EV charging
- EV inverters
- EV power conversion & OBC
- FCEV powertrain system
- Overview
- Automatic transmission hydraulic system
- Belt starter generator 48 V – inverter ISG
- Diesel direct injection
- Double-clutch transmission electrical control
- Double-clutch transmission hydraulic control
- Gasoline direct injection
- Multi-port fuel injection
- Small 1-cylinder combustion engine solution
- Small engine starter kit
- Transfer case brushed DC
- Transfer case brushless DC (BLDC)
- Overview
- Automotive head unit
- Automotive USB-C power & data solution
- Automotive instrument cluster
- Automotive telematics control unit (TCU)
- Center information display (CID)
- High-performance cockpit controller
- In-cabin wireless charging
- Smart instrument cluster (electric two- & three-wheelers)
- Overview
- E-bike solutions
- Two- & three-wheeler solutions
- Overview
- Audio amplifier solutions
- Complete system solutions for smart TVs
- Distribution audio amplifier unit solutions
- Home theater installation speaker system solutions
- Party speaker solutions
- PoE audio amplifier unit solutions
- Portable speaker solutions
- Powered active speaker systems
- Remote control
- Smart speaker designs
- Soundbar solutions
- Overview
- Data center and AI data center solutions
- Digital input/output (I/O) modules
- DIN rail power supply solutions
- Home and building automation
- Industrial HMI Monitors and Panels
- Industrial motor drives and controls
- Industrial PC
- Industrial robots system solutions for Industry 4.0
- Machine vision
- Mobile robots (AGV, AMR)
- Programmable logic controller (PLC)
- Solid-state circuit breaker
- Uninterruptible power supplies (UPS)
- Overview
- 48 V intermediate bus converter (IBC)
- AI accelerator cards
- AMD server CPUs
- Ampere CPUs
- FPGAs in datacenter applications
- Intel server CPUs
- Networking and switch platforms
- Power path protection
- Power system reliability modeling
- RAID storage
- Server battery backup units (BBU)
- Server power supply
- SmartNIC cards
- Overview
- AC-DC power conversion for telecommunications infrastructure
- DC-DC power conversion for telecommunications infrastructure
- FPGA in wired and wireless telecommunications applications
- Satellite communications
- Power system reliability modeling
- RF front end components for telecommunications infrastructure
- Overview
-
AC-DC power conversion
- Overview
- AC-DC auxiliary power supplies
- AC-DC power conversion for telecommunications infrastructure
- Adapters and chargers
- Automotive LED lighting systems
- Complete system solutions for smart TVs
- Desktop power supplies
- EV charging
- Industrial power supplies
- PoE power sourcing equipment (PSE)
- Server power supply units (PSU)
- Uninterruptible power supplies (UPS)
- DC-DC power conversion
- Overview
- Power supply health monitoring
- LATEST IN
- Digital documentation
- Evaluation boards
- Finder & selection tools
- Platforms
- Services
- Simulation & Modeling
- Software
- Tools
- Partners
- Infineon for Makers
- University Alliance Program
- Overview
- Bipolar Discs Finder
- Bipolar Module Finder
- Connected Secure Systems Finder
- Diode Rectifier Finder
- ESD Protection Finder
- Evaluation Board Finder
- Gate Driver Finder
- IGBT Discrete Finder
- IGBT Module Finder
- IPM Finder
- Microcontroller Finder
- MOSFET Finder
- PMIC Finder
- Product Finder
- PSOC™ and FMx MCU Board & Kit Finder
- Radar Finder
- Reference Design Finder
- Simulation Model Finder
- Smart Power Switch Finder
- Transceiver Finder
- Voltage Regulator Finder
- Wireless Connectivity Board & Kit Finder
- Overview
- AIROC™ software & tools
- AURIX™ software & tools
- DRIVECORE for automotive software development
- iMOTION™ software & tools
- Infineon Smart Power Switches & Gate Driver Tool Suite
- MOTIX™ software & tools
- OPTIGA™ software & tools
- PSOC™ software & tools
- TRAVEO™ software & tools
- XENSIV™ software & tools
- XMC™ software & tools
- Overview
- CoolGaN™ Simulation Tool (PLECS)
- HiRel Fit Rate Tool
- Infineon Designer
- Interactive product sheet
- IPOSIM Online Power Simulation Platform
- InfineonSpice Offline Simulation Tool
- OPTIREG™ automotive power supply ICs Simulation Tool (PLECS)
- Power MOSFET Simulation Models
- PowerEsim Switch Mode Power Supply Design Tool
- Solution Finder
- XENSIV™ Magnetic Sensor Simulation Tool
- Overview
- AURIX™ certifications
- AURIX™ development tools
-
AURIX™ Embedded Software
- Overview
- AURIX™ Applications software
- AURIX™ Artificial Intelligence
- AURIX™ Gateway
- AURIX™ iLLD Drivers
- Infineon safety
- AURIX™ Security
- AURIX™ TC3xx Motor Control Application Kit
- AURIX™ TC4x SW application architecture
- Infineon AUTOSAR
- Communication and Connectivity
- Middleware
- Non AUTOSAR OS/RTOS
- OTA
- AURIX™ Microcontroller Kits
- Overview
- TRAVEO™ Development Tools
- TRAVEO™ Embedded Software
- Overview
- XENSIV™ Development Tools
- XENSIV™ Embedded Software
- XENSIV™ evaluation boards
- Overview
- CAPSENSE™ Controllers Code Examples
- Memories for Embedded Systems Code Examples
- PSOC™ 1 Code Examples for PSOC™ Designer
- PSOC™ 3 Code Examples for PSOC™ Creator
- PSOC™ 3/4/5 Code Examples
- PSOC™ 4 Code Examples for PSOC™ Creator
- PSOC™ 6 Code Examples for PSOC™ Creator
- PSOC™ 63 Code Examples
- USB Controllers Code Examples
- Overview
- DEEPCRAFT™ AI Hub
- DEEPCRAFT™ Audio Enhancement
- DEEPCRAFT™ Model Converter
-
DEEPCRAFT™ Ready Models
- Overview
- DEEPCRAFT™ Ready Model for Baby Cry Detection
- DEEPCRAFT™ Ready Model for Cough Detection
- DEEPCRAFT™ Ready Model for Direction of Arrival (Sound)
- DEEPCRAFT™ Ready Model for Factory Alarm Detection
- DEEPCRAFT™ Ready Model for Fall Detection
- DEEPCRAFT™ Ready Model for Gesture Classification
- DEEPCRAFT™ Ready Model for Siren Detection
- DEEPCRAFT™ Ready Model for Snore Detection
- DEEPCRAFT™ Studio
- DEEPCRAFT™ Voice Assistant
- Overview
- AIROC™ Wi-Fi & Bluetooth EZ-Serial Module Firmware Platform
- AIROC™ Wi-Fi & Bluetooth Linux and Android Drivers
- emWin Graphics Library and GUI for PSOC™
- Infineon Complex Device Driver for Battery Management Systems
- Memory Solutions Hub
- PSOC™ 6 Peripheral Driver Library (PDL) for PSOC™ Creator
- USB Controllers EZ-USB™ GX3 Software and Drivers
- Overview
- CAPSENSE™ Controllers Configuration Tools EZ-Click
- DC-DC Integrated POL Voltage Regulators Configuration Tool – PowIRCenter
- EZ-USB™ SX3 Configuration Utility
- FM+ Configuration Tools
- FMx Configuration Tools
- Tranceiver IC Configuration Tool
- USB EZ-PD™ Configuration Utility
- USB EZ-PD™ Dock Configuration Utility
- USB EZ-USB™ HX3C Blaster Plus Configuration Utility
- USB UART Config Utility
- XENSIV™ Tire Pressure Sensor Programming
- Overview
- EZ-PD™ CCGx Dock Software Development Kit
-
FMx Softune IDE
- Overview
- RealOS™ Real-Time Operating System
- Softune IDE Language tools
- Softune Workbench
- Tool Lineup for F2MC-16 Family SOFTUNE V3
- Tool Lineup for F2MC-8FX Family SOFTUNE V3
- Tool Lineup for FR Family SOFTUNE V6
- Virtual Starter Kit
- Windows 10 operation of released SOFTUNE product
- Windows 7 operation of released SOFTUNE product
- Windows 8 operation of released SOFTUNE product
- ModusToolbox™ Software
- PSOC™ Creator Software
- Radar Development Kit
- RUST
- USB Controllers SDK
- Wireless Connectivity Bluetooth Mesh Helper Applications
- XMC™ DAVE™ Software
- Overview
- AIROC™ Bluetooth® Connect App Archive
- Cypress™ Programmer Archive
- EZ-PD™ CCGx Power Software Development Kit Archive
- ModusToolbox™ Software Archive
- PSOC™ Creator Archive
- PSOC™ Designer Archive
- PSOC™ Programmer Archive
- USB EZ-PD™ Configuration Utility Archives
- USB EZ-PD™ Host SDK Archives
- USB EZ-USB™ FX3 Archive
- USB EZ-USB™ HX3PD Configuration Utility Archive
- WICED™ Smart SDK Archive
- WICED™ Studio Archive
- Overview
- Infineon Developer Center Launcher
- Infineon Register Viewer
- Pin and Code Wizard
- Timing Solutions
- Wireless Connectivity
- LATEST IN
- Support
- Training
- Developer Community
- News
Business & Financial Press
Feb 04, 2026
Quarterly Report
Feb 04, 2026
Business & Financial Press
Feb 03, 2026
Business & Financial Press
Dec 16, 2025
- Company
- Our stories
- Events
- Press
- Investor
- Careers
- Quality
- Latest news
Business & Financial Press
Feb 04, 2026
Quarterly Report
Feb 04, 2026
Business & Financial Press
Feb 03, 2026
Business & Financial Press
Dec 16, 2025
Connected devices make our lives easier and more efficient. But with great connectivity comes great responsibility. As smart devices handle our personal data, manage our work, and even drive our cars, they may open the door to security risks. And now, with AI becoming a bigger part of our lives, security is more crucial than ever.
We understand that every use case has its own requirements. This is why we have designed Infineon Edge Protect to meet your unique security needs. It integrates leading security hardened and connected microcontrollers (MCU) from our PSOC™ and AIROC™ families, as well as discrete Secure Elements (dSE) from our OPTIGA™ and SECORA™ portfolios. Our hardware offering comes in combination with comprehensive security services such as cloud onboarding and late-stage provisioning.
Every device needs some type of MCU/MPU, but when should you extend your system with a discrete Secure Element? With Infineon Edge Protect we make it easy to choose the best fitting PSOC™ microcontrollers and to know when adding a discrete Secure Element can bring additional value.
1. Stay compliant with evolving regulations such as the Cyber Resilience Act (CRA)
2. Enhance interoperability across your systems
3. Gain a competitive edge and boost brand trust
4. Future-proof your products
5. Add value with NFC, payment, and late-stage provisioning capabilities
6. Reduce costs and minimize liability risks
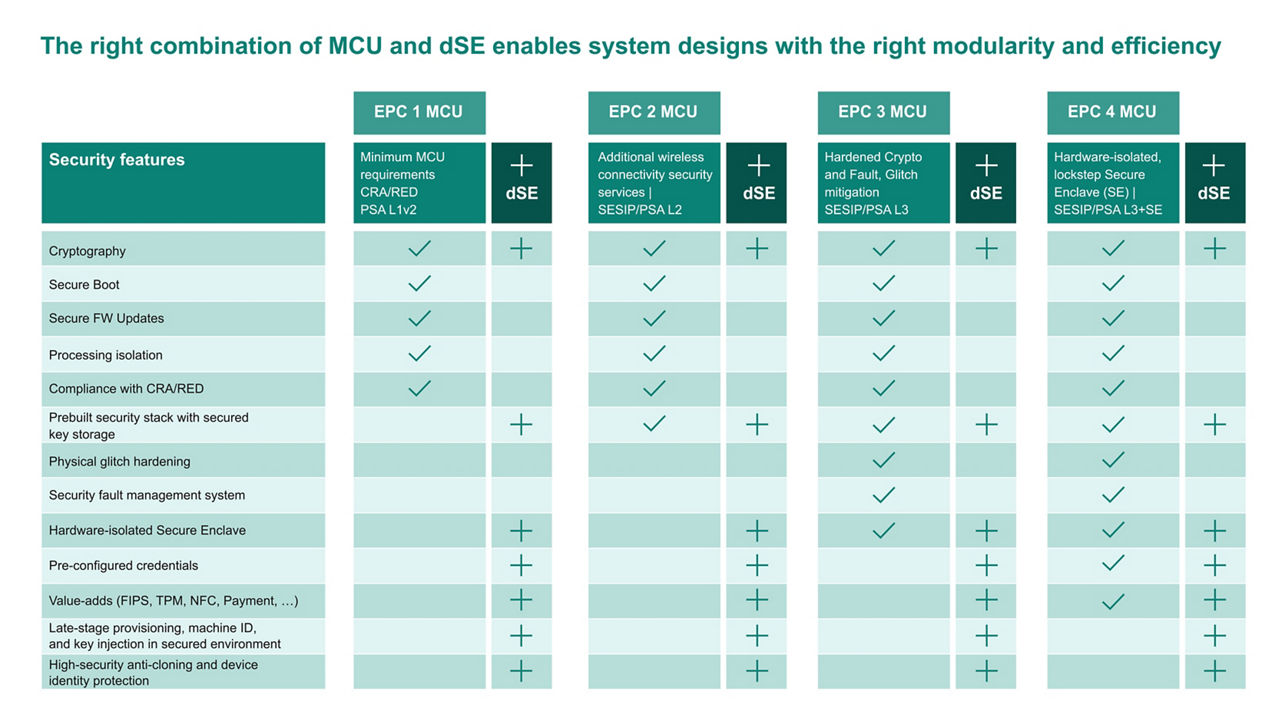
With the reference table, you can easily find out when a microcontroller on its own is a good match for your application and when you can gain an additional advantage by adding a discrete Secure Element. Our PSOC™ & AIROC™ microcontrollers offer robust security features, while our OPTIGA™ and SECORA™ discrete Secure Elements work in tandem with each PSOC™ to add value such as simplified manufacturing, improved efficiency, and long-term cost saving.
The table is divided into four Infineon Edge Protect categories (EPC) for simplified guidance.
- Edge Protect Category 1
Supports CRA and RED, PSA L1v2 - Edge Protect Category 2
Supports SESIP/PSA Level 2 - Edge Protect Category 3
Supports SESIP/PSA Level 3 - Edge Protect Category 4
Supports SESIP/PSA Level 3 + Secure Enclave


I need an easy and cost-efficient way to onboard my products
- In-house or in-the-field provisioning: In-house or in-the-field provisioning requires significant setup costs and specialized know-how, straining resources and budgets.
- Late-stage provisioning challenges: Provisioning devices at a late stage in the production process or in the field often poses significant logistical and security challenges.
- Protecting provisioning credentials: Ensuring the secured storage and management of provisioning credentials, both in the factory and in the field, is a critical concern to prevent unauthorized access and device cloning.
- Secured credential storage: Secured storage of provisioning credentials for late-state provisioning, protecting the integrity and confidentiality of sensitive information.
- Plug-and-play provisioning: Offering a plug-and-play provisioning solution, simplifying the process and reducing the need for specialized know-how.
- Cloud-based in-field provisioning: Providing a cloud-based system for in-the-field provisioning, enabling secured and efficient provisioning of devices at any stage.
- Cost-effective scalability: Delivering a cost-effective solution that scales with the needs of the business, minimizing costs and maximizing efficiency.


Example of a solution for smart home
- Easy to add Matter compatibility while keeping your existing design
- Flexibility add the DACs until the start of production and to create multiple product variants that can be released on the market quickly
- Matter certified with a Matter Attestation Certificate issued by our partner Kudelski IoT and approved by the CSA
- Common Criteria EAL6+ (high) certified hardware
I don’t trust my 3rd party supplier to manufacture only what I have ordered
- Unauthorized excess production: Contract manufacturers produce excess devices without permission, selling them into the grey market as "authentic" products.
- Tampered firmware, software, and configurations: Devices are altered before reaching the end customer, with changes to firmware, software, or configurations that can compromise security and functionality.
- Component fraud: High-value components, such as CPUs, GPUs, SSDs, and RAM, are replaced with cheaper alternatives, compromising device performance and reliability.
- Secured pre-provisioning: Pre-provisioning of certificates, keys, and device IDs in a secured environment, ensuring the integrity of devices from the start.
- Unique endorsement certificates: Provisioning of unique endorsement certificates in a certified environment, starting at the wafer level, to protect authenticity and trust.
- Immutable chip-ID: Ability to read out an immutable chip-ID, providing a secured and unique identifier for each device.


Example of a solution for securing the supply chain
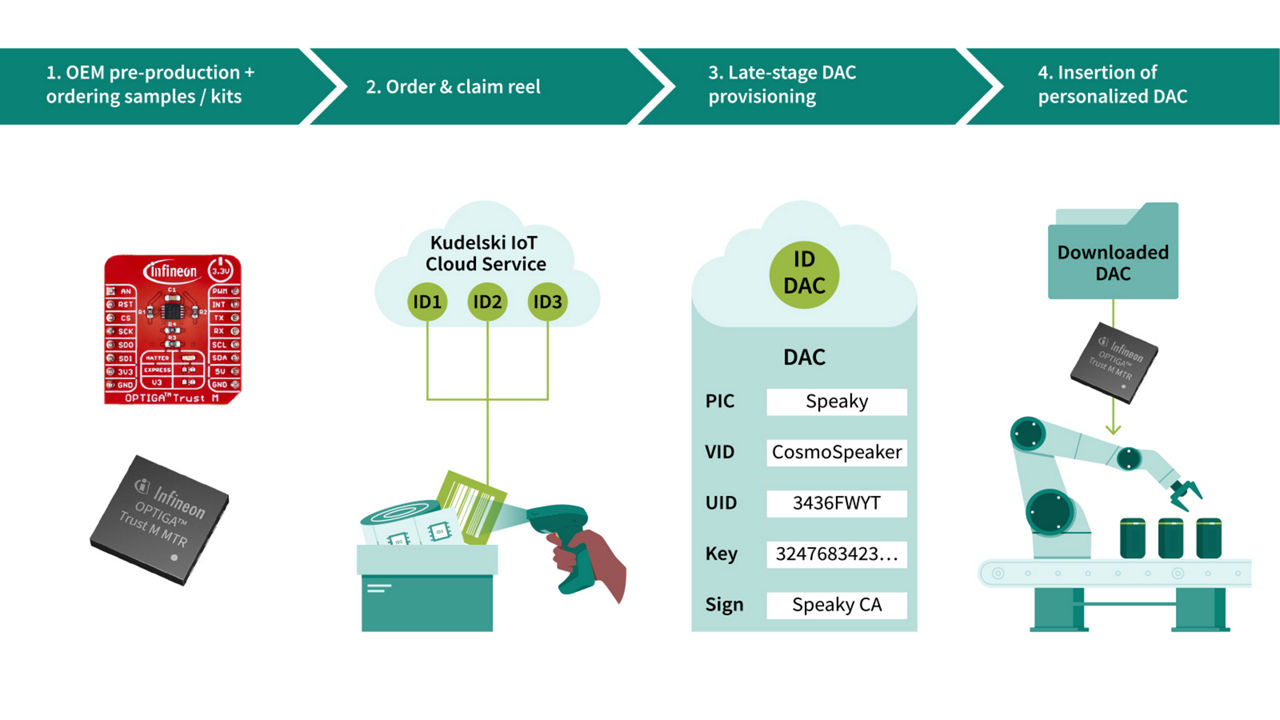
OPTIGA™ Trust M Express: the easiest way to securely deploy your IoT devices to the cloud - at scale
Key features
- Secured pre-provisioning of certificates, keys, and device IDs in a certified environment
- Provisioning of unique endorsement certificates at the wafer level
- Immutable chip-ID for secured and unique device identification
Benefits
- Automated cloud onboarding
- Simplified Device Customization
- Only Authenticated Devices attach to Product Cloud
My products are being cloned
Customer pain points
- Brand damage and liability: Clones can have safety issues, performance problems, or security breaches, resulting in costly recalls, lawsuits, and reputational harm.
- Device bricking: Lost or stolen devices must not be usable, even if they are original, to prevent unauthorized access and protect sensitive data.
- Refill fraud: Refilled or tampered consumables must be detected in the device, to maintain the quality of the output.
- Consumable counterfeiting: Counterfeit consumables, must not be usable in the device, preventing revenue loss and ensuring the quality of the output.
Necessary features
- Device blacklisting: Ability to blacklist devices when they are lost or stolen, preventing unauthorized access and use.
- Reverse engineering protection: Advanced security features that make reverse engineering significantly more complex.
- Cloud-based device activation: Cloud features for device activation and late provisioning so only authorized devices can be activated and used.
- Protected device identifier and authentication: Mechanisms that give each device a unique identity so it can be authenticated securely.
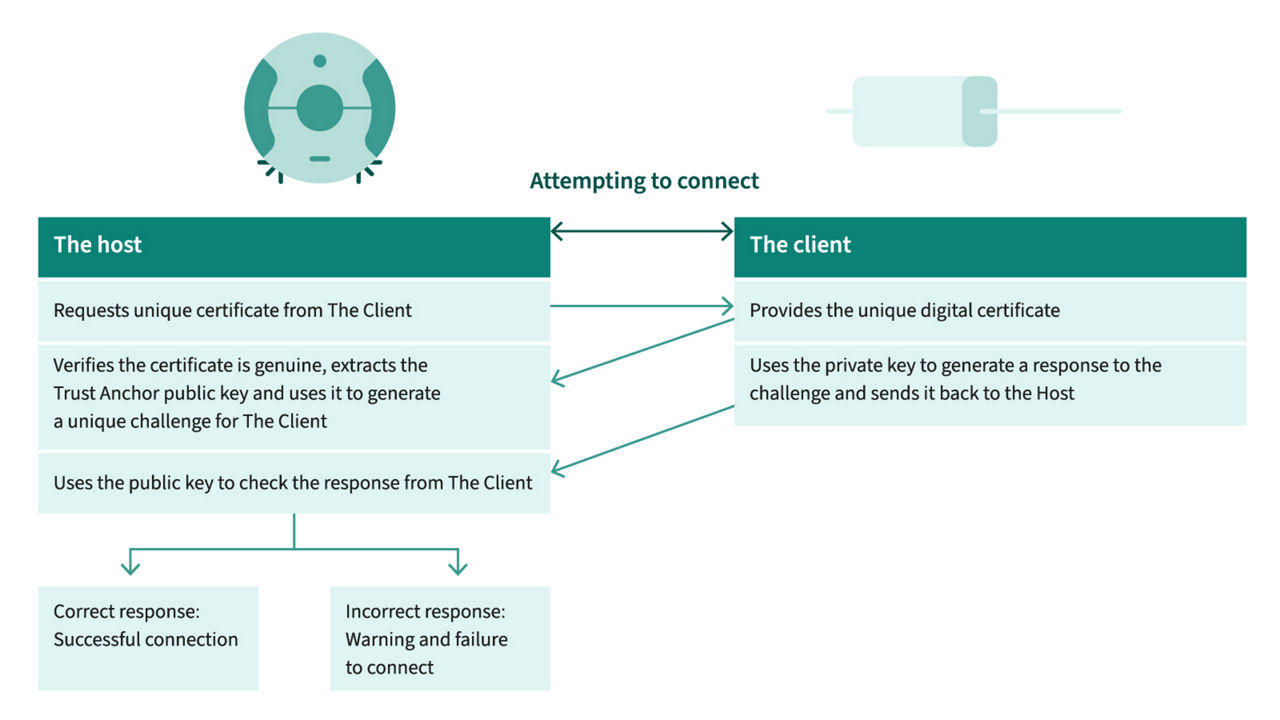
- Secured certificate-based authentication: A valid certificate and one-way authentication are required to include the device into the target system, with the authentication secret key stored and processed only in the Secure Element (SE).


Example of a solution for protection against cloning
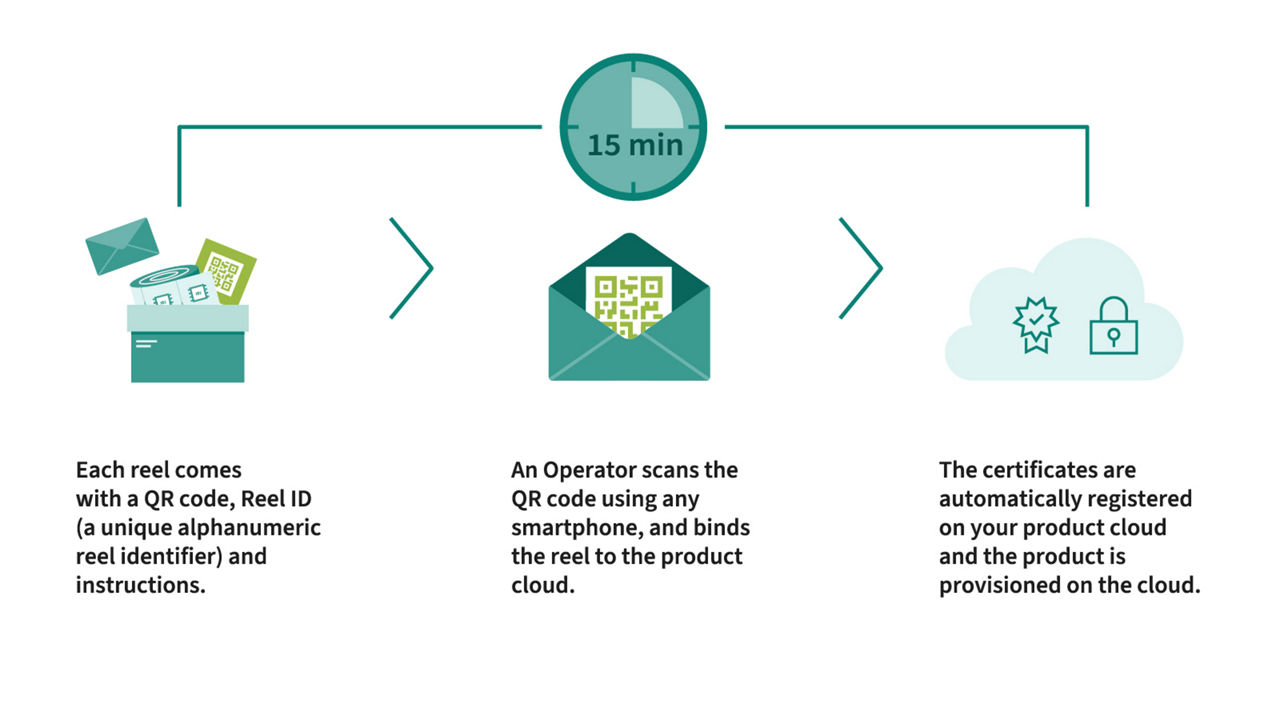
OPTIGA™ Authenticate S is a full turnkey solution that gives things a unique identity to verify their authenticity and to protect brands and their customers from counterfeits.
How it works
- Secured production
- Enabling tamper protection
- Secured implementation, storage and calculation
- Tracking of the value chain in a non-certified environment
- Reducing complexity and therefore time to market
Advantages of authentication
- 16 customization options
- Effortless implementation - full system integration support including embedded software, host software and advanced ecosystem support tools
- Freedom to design - tiny package of 1.5 mm² optimized for even the smallest devices
- Security to rely on
Why OPTIGA™ Authenticate S
- 16 customization options
- Effortless implementation - full system integration support including embedded software, host software and advanced ecosystem support tools
- Freedom to design - tiny package of 1.5 mm² optimized for even the smallest devices
- Security to rely on
My products are not flexible enough for changes (e.g., new MCU with same security framework)
Customer pain points
- Vendor lock-in: MCU security features are often vendor-specific, limiting flexibility and making it difficult to switch to a different MCU or vendor.
- Inflexibility for future capabilities: Devices are not flexible enough to accommodate new future capabilities, such as AI or low power requirements, making it difficult to adapt to changing market needs.
- Balancing security and MCU evolution: Security requirements need to be stable and well-tested, but MCU requirements are constantly changing, making it challenging to balance security with the need for innovation and adaptation.
Necessary features
- Plug-and-play security: Adding a Secure Element (SE) to the device for encapsulated security implementation and help to retain the same security system architecture and flexibility.
- Host library for MCU: For interaction with the SE is required, providing a standardized interface for communication and ensuring seamless integration.
- Scalable security: SE provides scalable security, enabling the implementation of different security levels and features depending on the specific device requirements.
- Future-proof security: The SE provides future-proof security, allowing for easy integration of new security features and algorithms as they become available.
- Standardized APIs: For easy integration with different MCUs and devices and to maintain the targeted security level.
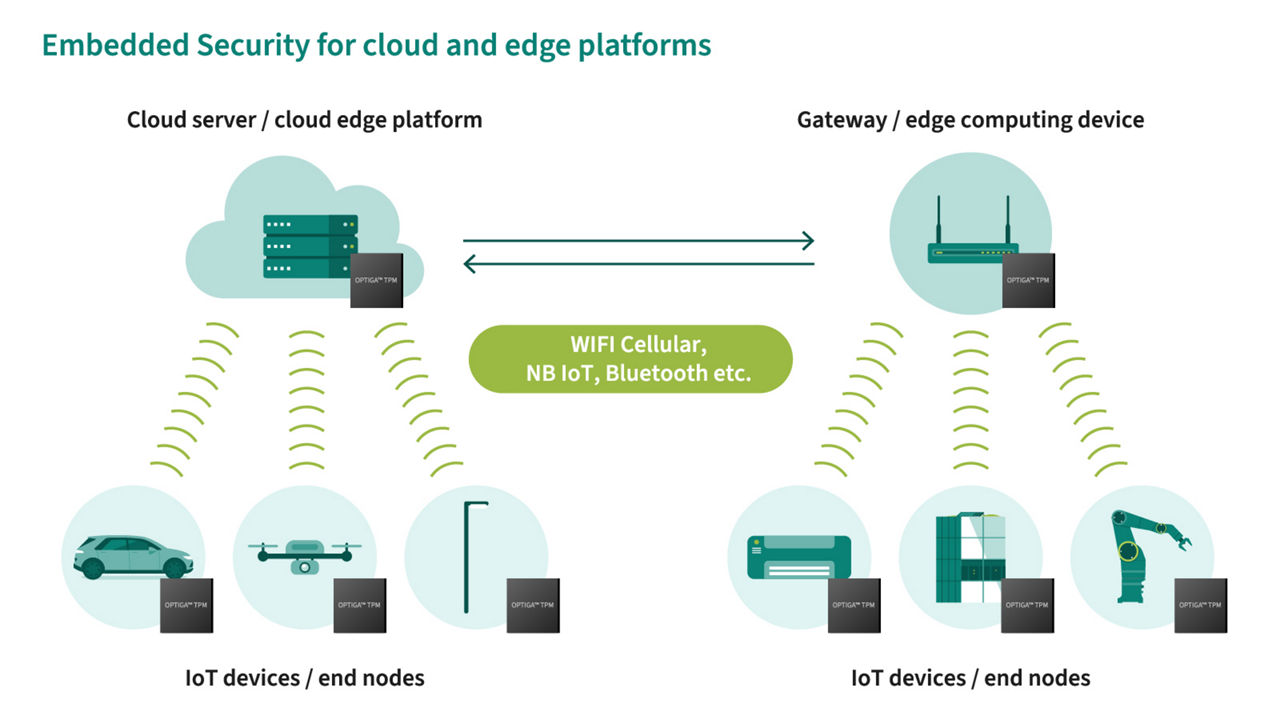


Example of a solution for protection against cloning
OPTIGA™ TPM provides maximum flexibility and no vendor lock-in with thanks to a standardized API.
Infineon’s OPTIGA™ TPM is certified for conformance with published TCG specifications with greater interoperability & flexibility
We produce high quality TPM products with various customization options and proven track record of more than 20 years.
I need to be compliant to various certifications and regulations (e.g. payment)
Customer pain points
- Navigating evolving cybersecurity regulations: Staying up-to-date with changing cybersecurity legislation and standards across different regions.
- Managing security requirements complexity: Understanding and fulfilling intricate security requirements, which demands significant resources and expertise.
- Designing future-proof secured products: Creating products that adapt to emerging threats and evolving security standards, maintaining customer trust and brand reputation.
Necessary features
- Streamlined system certification with comprehensive support: We provide all necessary documentation, reports, and support to simplify the system certification process, saving you time and resources.
- Expert design-in support for certification success: Our dedicated team provides guidance and support throughout the design-in process, ensuring a smooth and successful certification journey for your products.
- Simplified compliance with plug-and-play security: Easily integrate our Secure Element into your system for compliance with current and future legislation, without requiring extensive security expertise.



Example of a solution for compliance with regulations
SECORA™ Pay W: Best-in-class contactless performance enables the integration of payment functions in a wide variety of items.
- Flexible, one-stop-shop solution combining innovative technology with extensive services and design-in support
- Simple and fast integration of contactless payment functionality into innovative form factors
- Pre-certified by Visa and Mastercard and ready for implementation into innovative form factors
- Optimized for battery-less, passive wearables or payment accessories (key fobs, wristbands, bracelets, etc.)
- Based on SPA (Smart Payment Accessory) and can be integrated into almost every material
I need to manage the lifecycle of my product from production to end-of-life
Customer pain point
- End-of-life management: Managing the end-of-life of microcontrollers, to take care that they are securely decommissioned and that any sensitive data is erased.
- Secured field return analysis: Products may fail in the field due to various circumstances and methods are required to enable their analysis without compromising security.
Necessary features
- Hardware-based Root of Trust: A hardware-based root of trust provides a secured foundation for the boot process.
- Secure Boot mechanism: A Secure Boot mechanism prevents unauthorized firmware from being executed, preventing unauthorized access to the device.
- Digital signature verification: Digital signature verification capabilities allow for secured firmware authentication and validation.
- Secured key storage: Secure key storage protects cryptographic keys and prevents unauthorized access to sensitive data.
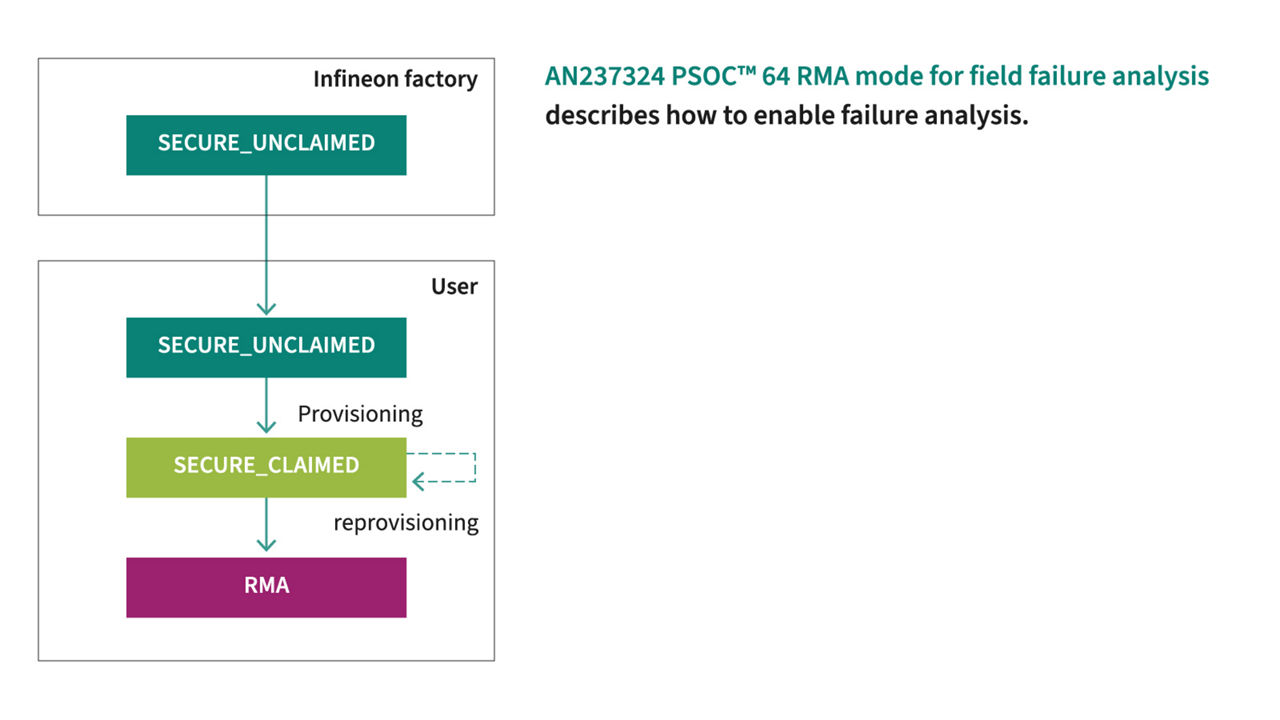
AN237324 PSOC™ 64 RMA mode for field failure analysis describes how to enable failure analysis.

AN237324 PSOC™ 64 RMA mode for field failure analysis describes how to enable failure analysis.

AN237324 PSOC™ 64 RMA mode for field failure analysis describes how to enable failure analysis.
Example of a solution for lifecycle management: RMA
In the event of a device failure or need for evaluation, a secured Return Merchandise Authorization (RMA) process is crucial to protect the integrity of your PSOC™ 64 MCU.
As a critical stage in the device lifecycle, RMA requires robust security measures to prevent unauthorized access, tampering, or theft of sensitive information.
By relying on the PSOC™ 64 secure RMA process you can:
- Prevent unauthorized access to sensitive data and intellectual property
- Protect the authenticity and integrity of returned devices
- Maintain compliance with industry regulations and standards
- Protect your brand reputation and customer trust
I need Secure Boot to prevent unauthorized software running on my product
Customer pain point
- Unauthorized software execution: Preventing unauthorized software from running on the device, to take care that only trusted and validated code is executed.
- Counterfeit firmware: Preventing counterfeit firmware from being installed on the device, to take care that only genuine and authorized firmware is used.
- Lack of visibility into running software: When it's unclear what software is running on a device, it becomes difficult to take care that only authorized software is executed and to detect potential security threats.
Necessary features
- Hardware-based Root of Trust: A hardware-based root of trust provides a secured foundation for the boot process.
- Secure Boot mechanism: A Secure Boot mechanism ensures only authorized firmware is executed, preventing unauthorized access to the device.
- Digital signature verification: Digital signature verification capabilities allow for secure firmware authentication and validation.
- Secured key storage: Secure key storage protects cryptographic keys and prevents unauthorized access to sensitive data.
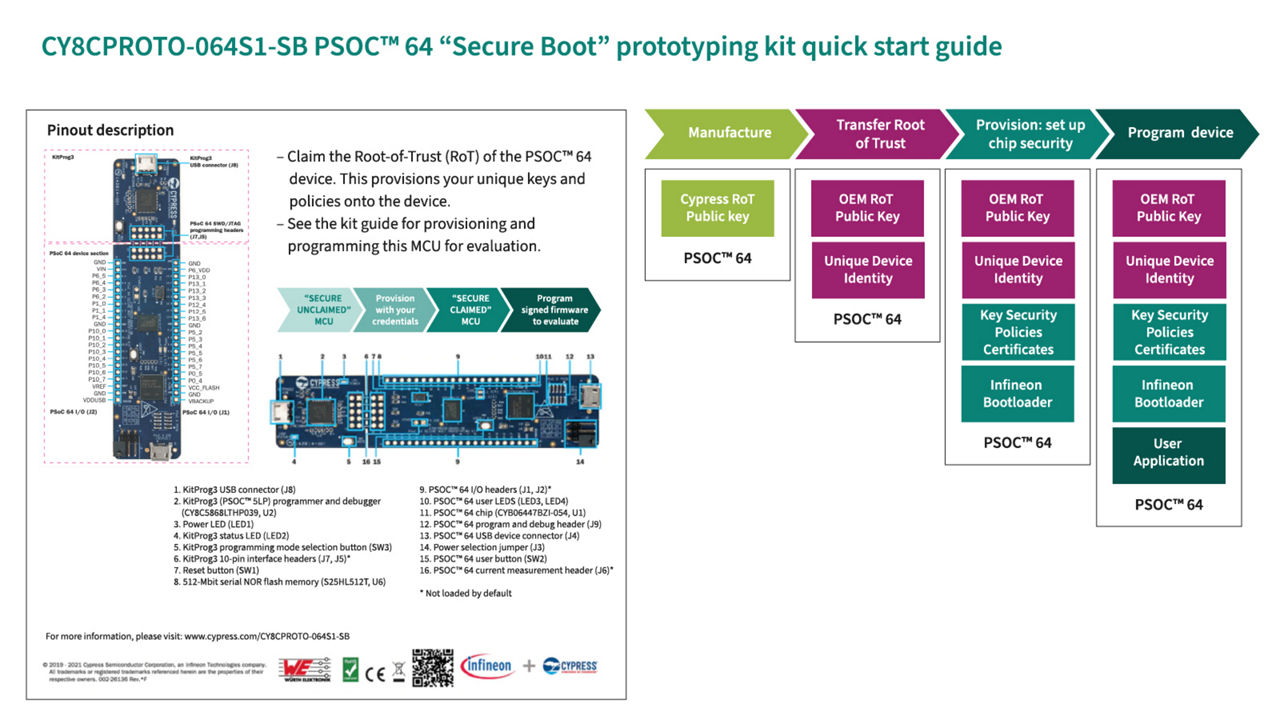


Example of a solution for Secure Boot
Infineon’s wide range of MCUs like PSOC™ support Secure Boot
Unlock the power of Secure Boot with our cutting-edge prototyping kit, designed to empower customers in implementing ironclad security measures with ease and efficiency. This comprehensive solution provides a seamless way to develop, test, and deploy Secure Boot solutions that meet highest standards of security and integrity.
My IP used in the product may get stolen (e.g. AI models)
Customer pain point
- IP theft: Preventing competitors and sub-contractors from stealing intellectual property (IP) from a device, to maintain a competitive advantage
- Code protection: Protecting code from being readable from the device, to prevent reverse engineering and IP theft
- Secure Updates: Enabling Secure Updates to the device, while preventing unauthorized access to IP
- Protection of investments: Protecting investments in software, algorithms, and other IP developments, to maintain a competitive edge
Necessary features
- Code and data protection: Read-out protection to prevent unauthorized access to code and data, taking care that sensitive information remains confidential
- Secure Updates: Encrypted updates to prevent tampering and protect authenticity, taking care that only authorized updates are applied to the device
- External storage protection: Authenticated encryption of external storage devices to prevent data theft and tampering, protecting sensitive data even when stored outside the device
- Debug interface protection: Protection and locking of debug interfaces and modes to prevent unauthorized access and IP theft, preventing attackers from exploiting debug interfaces to steal IP
- Logical attack protection: Protection against logical attacks, such as fault injection and side-channel attacks, to prevent IP theft and data breaches, protecting the device against these advanced attacks


Example of a solution for IP protection
Secured edge computing with PSOC™ Edge product family
Infineon's new PSOC Edge E8x MCU product family is designed to provide robust embedded security for Internet of Things (IoT) applications. The family has achieved the highest level of certification, PSA Certified Level 4, which ensures a hardware-isolated enclave on the chip for secure boot, key storage, and cryptographic operations.
The PSOC™ Edge product family addresses IP protection and Secure Update through its hardware-based security features. The devices feature protected crypto algorithms that can be used to encrypt critical IP, protecting sensitive information.
My software distributed over-the-air may get manipulated or stolen
Customer pain point
- Unintended device manipulation: Preventing firmware updates from being used for unintended device manipulation, such as malware injection or data theft.
- Scalable security: Taking care that unintended manipulation of devices is not scalable, to prevent widespread security breaches.
- Complex update process: Simplifying the complex process of firmware updates in the field, including key management and secure authentication.
- IP protection: Protecting intellectual property (IP) in firmware updates, to prevent theft and reverse engineering.
- Legacy device support: Easily extending legacy devices without sufficient resources, to provide continued security and support.
Necessary features
- Secured communication: Secured communication to a service, either over-the-air (OTA) or wired, to prevent eavesdropping and tampering.
- Integrity check: Integrity check on the device, using digital signatures, to take care that firmware updates are authentic and unmodified.
- Encryption: Encryption of firmware updates to prevent unauthorized access and provide confidentiality.
- Cloud service: Cloud service, including key management, to simplify and secure the firmware update process.
- Device identification & authentication: To check that firmware updates are sent to the correct device and to prevent unauthorized access.
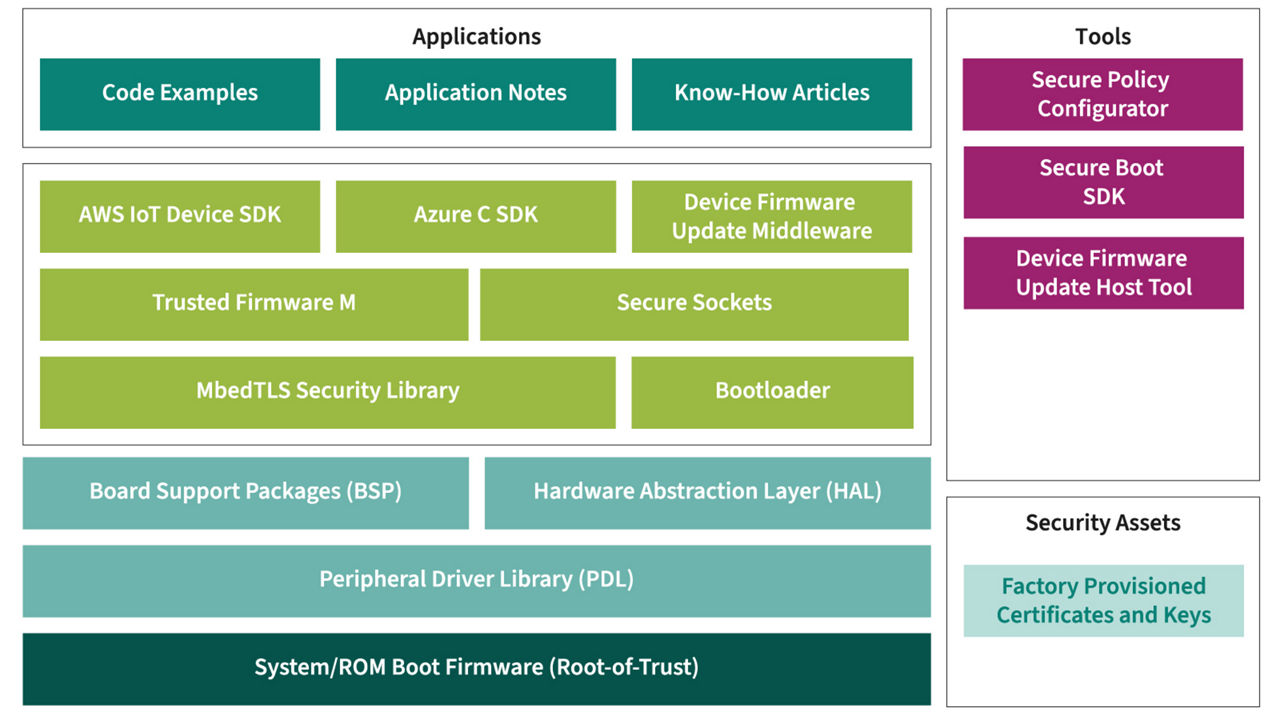


Example of a solution for software protection
With ModusToolbox™ for Security offers a comprehensive ecosystem of tools, middleware, libraries, code examples, user guides and application notes to facilitate the implementation of secured embedded systems.
Device firmware update
Middleware for connected and over-the-air (OTA) updates of its MCU lines. This supports connected serial interfaces as well as Wi-Fi and Bluetooth® and is complemented by a PC-based Host Tool. With the source code available, it can be adapted to specific customer requirements.
I have to optimize the overall cost position of my product
Customer pain point
- Balancing security and cost: Finding the right fit of security level with the best price point, to allow that security needs are met without breaking the bank.
- Meeting must-have security needs: Meeting minimum price points that can fulfill must-have security and feature needs, without sacrificing security or functionality.
- Limited security options: Only high-end MCUs with high prices have integrated security features, making it difficult to find a cost-effective solution that meets security needs.
- Complexity of security implementation: Implementing security features is complex and time-consuming, requiring significant expertise and resources.
Necessary features
- Low-cost security add-on: Lowest add-on in price to add security to the system, making it easy to integrate security without breaking the bank.
- Modular security architecture: Enable separation of the MCU functions from the security functions to gain a simple, scalable system with low price overall, allowing for easy integration and customization.
- Integrated security for high-end MCUs: Integrated security features in high-end SoCs, providing a comprehensive and robust security solution for demanding applications.
- Plug-and-play security: Adding security features must be easy to do, with a plug-and-play approach that simplifies integration and reduces development time.



Example of a solution for providing flexibility
With EPC we provide the flexibility to optimize the cost position overall by combining various MCUs with SE features to best address customer needs.
EPC allows to rely on IFX provided solutions (e.g., PSA Level 3) but also enables the customer to build cost efficient systems by adding a discrete Secure Element.
Do you have questions or need expert guidance on integrating our security solutions into your design? Our team is here to help. Reach out to us to discuss your project and let us support you in bringing your vision to life.
Stay up-to-date on the latest security trends, product releases, and announcements about Infineon Edge Protect. Subscribe now and get instant access to exclusive updates, insights, and resources to help you stay ahead of the curve in security.
