- ASIC
- Battery management ICs
- Clocks and timing solutions
- ESD and surge protection devices
- Automotive Ethernet
- Evaluation Boards
- High reliability
- Isolation
- Memories
- Microcontroller
- Power
- RF
- Security and smart card solutions
- Sensor technology
- Small signal transistors and diodes
- Transceivers
- Universal Serial Bus (USB)
- Wireless connectivity
- Suchwerkzeuge
- Packages
- Bezugsquellen
- Überblick
- Automotive Ethernet Bridges
- Automotive Ethernet PHY for in-vehicle networking
- Automotive Ethernet Switches for in-vehicle networking
- Überblick
- Defense
- High-reliability custom services
- NewSpace
- Space
- Überblick
- Embedded flash IP solutions
- Flash+RAM MCP solutions
- F-RAM (Ferroelectric RAM)
- NOR flash
- nvSRAM (non-volatile SRAM)
- PSRAM (Pseudostatic RAM)
- Radiation hardened and high-reliability memories
- RRAM Resistive Ram
- SRAM (static RAM)
- Wafer and die memory solutions
- Überblick
- 32-bit FM Arm® Cortex® Microcontroller
- 32-bit AURIX™ TriCore™ microcontroller
- 32-bit PSOC™ Arm® Cortex® microcontroller
- 32-bit TRAVEO™ T2G Arm® Cortex® microcontroller
- 32-bit XMC™ industrial microcontroller Arm® Cortex®-M
- Legacy microcontroller
- MOTIX™ MCU | 32-bit motor control SoC based on Arm® Cortex®-M
- Sensing controllers
- Überblick
- AC-DC power conversion
- Automotive conventional powertrain ICs
- Class D audio amplifier ICs
- Contactless power and sensing ICs
- DC-DC converters
- Diodes and thyristors (Si/SiC)
- Gallium nitride (GaN)
- Gate driver ICs
- IGBTs – Insulated gate bipolar transistors
- Intelligent power modules (IPM)
- LED driver ICs
- Motor control ICs
- Power MOSFETs
- Power modules
- Power supply ICs
- Protection and monitoring ICs
- Silicon carbide (SiC)
- Smart power switches
- Solid state relays
- Wireless charging ICs
- Überblick
- Antenna cross switches
- Antenna tuners
- Bias and control
- Coupler
- Driver amplifiers
- High Reliability Discrete
- Low noise amplifiers (LNAs)
- RF diode
- RF switches
- RF transistors
- Wireless control receiver
- Überblick
- Calypso® products
- CIPURSE™ products
- Contactless memories
- OPTIGA™ embedded security solutions
- SECORA™ security solutions
- Security controllers
- Smart card modules
- Smart solutions for government ID
- Überblick
- ToF 3D image sensors
- Current sensors
- Gas sensors
- Inductive position sensors
- MEMS microphones
- Pressure sensors
- Radar sensors
- Magnetic position sensors
- Magnetic speed sensors
- Überblick
- Bipolar transistors
- Diodes
- Small signal/small power MOSFET
- Überblick
- Automotive transceivers
- Control communication
- Powerline communications
- Überblick
- USB 2.0 peripheral controllers
- USB 3.2 peripheral controllers
- USB hub controllers
- USB PD high-voltage microcontrollers
- USB-C AC-DC and DC-DC charging solutions
- USB-C charging port controllers
- USB-C Power Delivery controllers
- Überblick
- AIROC™ Automotive wireless
- AIROC™ Bluetooth® and multiprotocol
- AIROC™ connected MCU
- AIROC™ Wi-Fi + Bluetooth® combos
- Überblick
- Commercial off-the-shelf (COTs) memory portfolio
- Defense memory portfolio
- High-reliability power conversion and management
- Überblick
- NewSpace memory portfolio
- Radiation tolerant power
- Überblick
- Rad hard microwave and RF
- Radiation hardened power
- Space memory portfolio
- Überblick
- Parallel NOR flash
- SEMPER™ NOR flash family
- SEMPER™ X1 LPDDR flash
- Serial NOR flash
- Überblick
- FM0+ 32-bit Arm® Cortex®-M0+ microcontroller (MCU) families
-
FM3 32-bit Arm® Cortex®-M3 microcontroller (MCU) families
- Überblick
- FM3 CY9AFx1xK series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx1xL/M/N series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx2xK/L series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx3xK/L series ultra-low leak Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx4xL/M/N series low power Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFx5xM/N/R series low power Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9AFxAxL/M/N series ultra-low leak Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx1xN/R high-performance series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx1xS/T high-performance series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx2xJ series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx2xK/L/M series Arm® Cortex®-M3 microcontroller (MCU)
- FM3 CY9BFx2xS/T series Arm® Cortex®-M3 microcontroller (MCU)
-
FM4 32-bit Arm® Cortex®-M4 microcontroller (MCU) families
- Überblick
- FM4 CY9BFx6xK/L high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- FM4 CY9BFx6xM/N/R high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- FM4 S6E2C high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- FM4 S6E2G series connectivity Arm® Cortex®-M4F microcontroller (MCU)
- FM4 S6E2H high-performance series Arm® Cortex®-M4F microcontroller (MCU)
- Überblick
-
32-bit TriCore™ AURIX™ – TC2x
- Überblick
- AURIX™ family – TC21xL
- AURIX™ family – TC21xSC (wireless charging)
- AURIX™ family – TC22xL
- AURIX™ family – TC23xL
- AURIX™ family – TC23xLA (ADAS)
- AURIX™ family – TC23xLX
- AURIX™ family – TC264DA (ADAS)
- AURIX™ family – TC26xD
- AURIX™ family – TC27xT
- AURIX™ family – TC297TA (ADAS)
- AURIX™ family – TC29xT
- AURIX™ family – TC29xTT (ADAS)
- AURIX™ family – TC29xTX
- AURIX™ TC2x emulation devices
-
32-bit TriCore™ AURIX™ – TC3x
- Überblick
- AURIX™ family - TC32xLP
- AURIX™ family – TC33xDA
- AURIX™ family - TC33xLP
- AURIX™ family – TC35xTA (ADAS)
- AURIX™ family – TC36xDP
- AURIX™ family – TC37xTP
- AURIX™ family – TC37xTX
- AURIX™ family – TC38xQP
- AURIX™ family – TC39xXA (ADAS)
- AURIX™ family – TC39xXX
- AURIX™ family – TC3Ex
- AURIX™ TC37xTE (emulation devices)
- AURIX™ TC39xXE (emulation devices)
- 32-bit TriCore™ AURIX™ – TC4x
- Überblick
- PSOC™ 4 Arm® Cortex®-M0/M0+
- PSOC™ 4 HV Arm® Cortex®-M0+
- PSOC™ 5 LP Arm® Cortex®-M3
- PSOC™ 6 Arm® Cortex®-M4/M0+
- PSOC™ Multitouch Arm® Cortex®-M0
- PSOC™ Control Arm® Cortex®-M33
- PSOC™ Fingerprint Arm® Cortex®-M0+
- PSOC™ Automotive 4: Arm® Cortex®-M0/M0+
- PSOC™ Edge Arm® Cortex® M55/M33
- Überblick
- 32-bit TRAVEO™ T2G Arm® Cortex® for body
- 32-bit TRAVEO™ T2G Arm® Cortex® for cluster
- Überblick
- 32-bit XMC1000 industrial microcontroller Arm® Cortex®-M0
- 32-bit XMC4000 industrial microcontroller Arm® Cortex®-M4
- XMC5000 Industrial Microcontroller Arm® Cortex®-M4F
- 32-bit XMC7000 Industrial Microcontroller Arm® Cortex®-M7
- Überblick
- Legacy 32-bit MCU
- Legacy 8-bit/16-bit microcontroller
- Other legacy MCUs
- Überblick
- AC-DC integrated power stage - CoolSET™
- AC-DC PWM-PFC controller
- Überblick
- Bridge rectifiers & AC switches
- CoolSiC™ Schottky diodes
- Diode bare dies
- Silicon diodes
- Thyristor / Diode Power Modules
- Thyristor soft starter modules
- Thyristor/diode discs
- Überblick
- Automotive gate driver ICs
- Isolated Gate Driver ICs
- Level-Shift Gate Driver ICs
- Low-Side Drivers
- Transformer Driver ICs
- Überblick
- AC-DC LED driver ICs
- Ballast IC
- DC-DC LED driver IC
- LED dimming interface IC
- Linear LED driver IC
- LITIX™ - Automotive LED Driver IC
- NFC wireless configuration IC with PWM output
- VCSEL driver
- Überblick
- 32-bit PSOC™ Control Arm® Cortex®-M33 MCU
- iMOTION™ Integrated motor control solutions
- MOTIX™ MCU | 32-bit motor control SoC based on Arm® Cortex®-M
- MOTIX™ motor control ICs for BLDC motors
- MOTIX™ motor control ICs for brushed DC motors
- MOTIX™ multi half-bridge ICs for servo and stepper motors
- Überblick
- Automotive MOSFET
- Dual MOSFETs
- MOSFET (Si & SiC) Modules
- N-channel depletion mode MOSFET
- N-channel MOSFETs
- P-channel power MOSFETs
- Silicon carbide CoolSiC™ MOSFETs
- Small signal/small power MOSFET
- Überblick
- Automotive transceivers
- Linear Voltage Regulators for Automotive Applications
- OPTIREG™ PMIC
- OPTIREG™ switcher
- OPTIREG™ System Basis Chips (SBC)
- Überblick
- eFuse
-
High-side switches
- Überblick
- Classic PROFET™ 12V | Automotive smart high-side switch
- Classic PROFET™ 24V | Automotive smart high-side switch
- Power PROFET™ + 12/24/48V | Automotive smart high-side switch
- PROFET™ + 12V | Automotive smart high-side switch
- PROFET™ + 24V | Automotive smart high-side switch
- PROFET™ + 48V | Automotive smart high-side switch
- PROFET™ +2 12V | Automotive smart high-side switch
- PROFET™ Industrial | Smart high-side switch
- PROFET™ Load Guard 12V | Automotive smart high-side switch
- PROFET™ Wire Guard 12V | Automotive eFuse
- Low-side switches
- Multichannel SPI Switches & Controller
- Überblick
- Radar sensors for automotive
- Radar sensors for IoT
- Überblick
- EZ-USB™ CX3 MIPI CSI2 to USB 3.0 camera controller
- EZ-USB™ FX10 & FX5N USB 10Gbps peripheral controller
- EZ-USB™ FX20 USB 20 Gbps peripheral controller
- EZ-USB™ FX3 USB 5 Gbps peripheral controller
- EZ-USB™ FX3S USB 5 Gbps peripheral controller with storage interface
- EZ-USB™ FX5 USB 5 Gbps peripheral controller
- EZ-USB™ SD3 USB 5 Gbps storage controller
- EZ-USB™ SX3 FIFO to USB 5 Gbps peripheral controller
- Überblick
- EZ-PD™ CCG3 USB type-C port controller PD
- EZ-PD™ CCG3PA USB-C and PD
- EZ-PD™ CCG3PA-NFET USB-C PD controller
- EZ-PD™ CCG7x consumer USB-C Power Delivery & DC-DC controller
- EZ-PD™ PAG1: power adapter generation 1
- EZ-PD™ PAG2: Power Adapter Generation 2
- EZ-PD™ PAG2-PD USB-C PD Controller
- Überblick
- EZ-PD™ ACG1F one-port USB-C controller
- EZ-PD™ CCG2 USB Type-C port controller
- EZ-PD™ CCG3PA Automotive USB-C and Power Delivery controller
- EZ-PD™ CCG4 two-port USB-C and PD
- EZ-PD™ CCG5 dual-port and CCG5C single-port USB-C PD controllers
- EZ-PD™ CCG6 one-port USB-C & PD controller
- EZ-PD™ CCG6_CFP and EZ-PD™ CCG8_CFP Dual-Single-Port USB-C PD
- EZ-PD™ CCG6DF dual-port and CCG6SF single-port USB-C PD controllers
- EZ-PD™ CCG7D Automotive dual-port USB-C PD + DC-DC controller
- EZ-PD™ CCG7S Automotive single-port USB-C PD solution with a DC-DC controller
- EZ-PD™ CCG7SAF Automotive Single-port USB-C PD + DC-DC Controller + FETs
- EZ-PD™ CCG8 dual-single-port USB-C PD
- EZ-PD™ CMG1 USB-C EMCA controller
- EZ-PD™ CMG2 USB-C EMCA controller with EPR
- AKTUELLES IN
- Aerospace and defense
- Automotive
- Consumer electronics
- Health and lifestyle
- Home appliances
- Industrial
- Information and Communication Technology
- Renewables
- Robotics
- Security solutions
- Smart home and building
- Solutions
- Überblick
- Defense applications
- Space applications
- Überblick
- 48 V systems for EVs & mild hybrids
- ADAS & autonomous driving
- Automotive body electronics & power distribution
- Automotive LED lighting systems
- Chassis control & safety
- Electric vehicle drivetrain system
- EV thermal management system
- Internal combustion drivetrain systems
- In-vehicle infotainment & HMI
- Light electric vehicle solutions
- Überblick
- Adapters and chargers
- Complete system solutions for smart TVs
- Mobile device and smartphone solutions
- Multicopters and drones
- Power tools
- Semiconductor solutions for home entertainment applications
- Smart conference systems
- Überblick
- Adapters and chargers
- Asset Tracking
- Battery formation and testing
- Electric forklifts
- Battery energy storage (BESS)
- EV charging
- High voltage solid-state power distribution
- Industrial automation
- Industrial motor drives and controls
- Industrial robots system solutions for Industry 4.0
- LED lighting system design
- Light electric vehicle solutions
- Power tools
- Power transmission and distribution
- Traction
- Uninterruptible power supplies (UPS)
- Überblick
- Data center and AI data center solutions
- Edge computing
- Telecommunications infrastructure
- Machine Learning Edge AI
- Überblick
- Battery formation and testing
- EV charging
- Hydrogen
- Photovoltaic
- Wind power
- Solid-state circuit breaker
- Battery energy storage (BESS)
- Überblick
- Device authentication and brand protection
- Embedded security for the Internet of Things (IoT)
- eSIM applications
- Government identification
- Mobile security
- Payment solutions
- Access control and ticketing
- Überblick
- Domestic robots
- Heating ventilation and air conditioning (HVAC)
- Home and building automation
- PC accessories
- Semiconductor solutions for home entertainment applications
- Überblick
- Battery management systems (BMS)
- Connectivity
- Human Machine Interface
- Machine Learning Edge AI
- Motor control
- Power conversion
- Security
- Sensor solutions
- System diagnostics and analytics
- Überblick
- Automotive auxiliary systems
- Automotive gateway
- Automotive power distribution
- Body control modules (BCM)
- Comfort & convenience electronics
- Zonal DC-DC converter 48 V-12 V
- Zone control unit
- Überblick
- Automotive animated LED lighting system
- Automotive LED front single light functions
- Automotive LED rear single light functions
- Full LED headlight system - multi-channel LED driver
- LED drivers (electric two- & three-wheelers)
- LED pixel light controller - supply & communication
- Static interior ambient LED light
- Überblick
- Active suspension control
- Airbag system
- Automotive braking solutions
- Automotive steering solutions
- Chassis domain control
- Reversible seatbelt pretensioner
- Überblick
-
Automotive BMS
- Überblick
- Automotive battery cell monitoring & balancing
- Automotive battery control unit (BCU)
- Automotive battery isolated communication
- Automotive battery management system (BMS) - 12 V to 24 V
- Automotive battery management system (BMS) - 48 V
- Automotive battery management system (BMS) - high-voltage
- Automotive battery pack monitoring
- Automotive battery passport & event logging
- Automotive battery protection & disconnection
- Automotive current sensing & coulomb counting
- BMS (electric two- & three-wheelers)
- EV charging
- EV inverters
- EV power conversion & OBC
- FCEV powertrain system
- Überblick
- Automatic transmission hydraulic system
- Belt starter generator 48 V – inverter ISG
- Diesel direct injection
- Double-clutch transmission electrical control
- Double-clutch transmission hydraulic control
- Gasoline direct injection
- Multi-port fuel injection
- Small 1-cylinder combustion engine solution
- Small engine starter kit
- Transfer case brushed DC
- Transfer case brushless DC (BLDC)
- Überblick
- Automotive head unit
- Automotive USB-C power & data solution
- Automotive instrument cluster
- Automotive telematics control unit (TCU)
- Center information display (CID)
- High-performance cockpit controller
- In-cabin wireless charging
- Smart instrument cluster (electric two- & three-wheelers)
- Überblick
- E-bike solutions
- Two- & three-wheeler solutions
- Überblick
- Audio amplifier solutions
- Complete system solutions for smart TVs
- Distribution audio amplifier unit solutions
- Home theater installation speaker system solutions
- Party speaker solutions
- PoE audio amplifier unit solutions
- Portable speaker solutions
- Powered active speaker systems
- Remote control
- Smart speaker designs
- Soundbar solutions
- Überblick
- Data center and AI data center solutions
- Digital input/output (I/O) modules
- DIN rail power supply solutions
- Home and building automation
- Industrial HMI Monitors and Panels
- Industrial motor drives and controls
- Industrial PC
- Industrial robots system solutions for Industry 4.0
- Industrial sensors
- Machine vision
- Mobile robots (AGV, AMR)
- Programmable logic controller (PLC)
- Solid-state circuit breaker
- Uninterruptible power supplies (UPS)
- Überblick
- 48 V intermediate bus converter (IBC)
- AI accelerator cards
- AMD server CPUs
- Ampere CPUs
- FPGAs in datacenter applications
- Intel server CPUs
- Networking and switch platforms
- Power path protection
- Power system reliability modeling
- RAID storage
- Server battery backup units (BBU)
- Server power supply
- SmartNIC cards
- Überblick
- AC-DC power conversion for telecommunications infrastructure
- DC-DC power conversion for telecommunications infrastructure
- FPGA in wired and wireless telecommunications applications
- Satellite communications
- Power system reliability modeling
- RF front end components for telecommunications infrastructure
- Überblick
-
AC-DC power conversion
- Überblick
- AC-DC auxiliary power supplies
- AC-DC power conversion for telecommunications infrastructure
- Adapters and chargers
- Automotive LED lighting systems
- Complete system solutions for smart TVs
- Desktop power supplies
- EV charging
- Industrial power supplies
- PoE power sourcing equipment (PSE)
- Server power supply units (PSU)
- Uninterruptible power supplies (UPS)
- DC-DC power conversion
- Überblick
- Power supply health monitoring
- AKTUELLES IN
- Digital documentation
- Evaluation boards
- Finder & selection tools
- Platforms
- Services
- Simulation & Modeling
- Software
- Tools
- Partners
- Maker
- University Alliance Program
- Überblick
- Bipolar Discs Finder
- Bipolar Module Finder
- Connected Secure Systems Finder
- Diode Rectifier Finder
- ESD Protection Finder
- Evaluation Board Finder
- Gate Driver Finder
- IGBT Discrete Finder
- IGBT Module Finder
- IPM Finder
- Microcontroller Finder
- MOSFET Finder
- PMIC Finder
- Product Finder
- PSOC™ and FMx MCU Board & Kit Finder
- Radar Finder
- Reference Design Finder
- Simulation Model Finder
- Smart Power Switch Finder
- Transceiver Finder
- Voltage Regulator Finder
- Wireless Connectivity Board & Kit Finder
- Überblick
- AIROC™ software & tools
- AURIX™ software & tools
- DRIVECORE for automotive software development
- iMOTION™ software & tools
- Infineon Smart Power Switches & Gate Driver Tool Suite
- MOTIX™ software & tools
- OPTIGA™ software & tools
- PSOC™ software & tools
- TRAVEO™ software & tools
- XENSIV™ software & tools
- XMC™ software & tools
- Überblick
- CoolGaN™ Simulation Tool (PLECS)
- HiRel Fit Rate Tool
- Infineon Designer
- Interactive product sheet
- IPOSIM Online Power Simulation Platform
- InfineonSpice Offline Simulation Tool
- OPTIREG™ automotive power supply ICs Simulation Tool (PLECS)
- Power MOSFET Simulation Models
- PowerEsim Switch Mode Power Supply Design Tool
- Solution Finder
- XENSIV™ Magnetic Sensor Simulation Tool
- Überblick
- AURIX™ certifications
- AURIX™ development tools
-
AURIX™ Embedded Software
- Überblick
- AURIX™ Applications software
- AURIX™ Artificial Intelligence
- AURIX™ Gateway
- AURIX™ iLLD Drivers
- Infineon safety
- AURIX™ Security
- AURIX™ TC3xx Motor Control Application Kit
- AURIX™ TC4x SW application architecture
- Infineon AUTOSAR
- Communication and Connectivity
- Middleware
- Non AUTOSAR OS/RTOS
- OTA
- AURIX™ Microcontroller Kits
- Überblick
- TRAVEO™ Development Tools
- TRAVEO™ Embedded Software
- Überblick
- XENSIV™ Development Tools
- XENSIV™ Embedded Software
- XENSIV™ evaluation boards
- Überblick
- CAPSENSE™ Controllers Code Examples
- Memories for Embedded Systems Code Examples
- PSOC™ 1 Code Examples for PSOC™ Designer
- PSOC™ 3 Code Examples for PSOC™ Creator
- PSOC™ 3/4/5 Code Examples
- PSOC™ 4 Code Examples for PSOC™ Creator
- PSOC™ 6 Code Examples for PSOC™ Creator
- PSOC™ 63 Code Examples
- USB Controllers Code Examples
- Überblick
- DEEPCRAFT™ AI Hub
- DEEPCRAFT™ Audio Enhancement
- DEEPCRAFT™ Model Converter
-
DEEPCRAFT™ Ready Models
- Überblick
- DEEPCRAFT™ Ready Model for Baby Cry Detection
- DEEPCRAFT™ Ready Model for Cough Detection
- DEEPCRAFT™ Ready Model for Direction of Arrival (Sound)
- DEEPCRAFT™ Ready Model for Factory Alarm Detection
- DEEPCRAFT™ Ready Model for Fall Detection
- DEEPCRAFT™ Ready Model for Gesture Classification
- DEEPCRAFT™ Ready Model for Siren Detection
- DEEPCRAFT™ Ready Model for Snore Detection
- DEEPCRAFT™ Studio
- DEEPCRAFT™ Voice Assistant
- Überblick
- AIROC™ Wi-Fi & Bluetooth EZ-Serial Module Firmware Platform
- AIROC™ Wi-Fi & Bluetooth Linux and Android Drivers
- emWin Graphics Library and GUI for PSOC™
- Infineon Complex Device Driver for Battery Management Systems
- Memory Solutions Hub
- PSOC™ 6 Peripheral Driver Library (PDL) for PSOC™ Creator
- USB Controllers EZ-USB™ GX3 Software and Drivers
- Überblick
- CAPSENSE™ Controllers Configuration Tools EZ-Click
- DC-DC Integrated POL Voltage Regulators Configuration Tool – PowIRCenter
- EZ-USB™ SX3 Configuration Utility
- FM+ Configuration Tools
- FMx Configuration Tools
- Tranceiver IC Configuration Tool
- USB EZ-PD™ Configuration Utility
- USB EZ-PD™ Dock Configuration Utility
- USB EZ-USB™ HX3C Blaster Plus Configuration Utility
- USB UART Config Utility
- XENSIV™ Tire Pressure Sensor Programming
- Überblick
- EZ-PD™ CCGx Dock Software Development Kit
-
FMx Softune IDE
- Überblick
- RealOS™ Real-Time Operating System
- Softune IDE Language tools
- Softune Workbench
- Tool Lineup for F2MC-16 Family SOFTUNE V3
- Tool Lineup for F2MC-8FX Family SOFTUNE V3
- Tool Lineup for FR Family SOFTUNE V6
- Virtual Starter Kit
- Windows 10 operation of released SOFTUNE product
- Windows 7 operation of released SOFTUNE product
- Windows 8 operation of released SOFTUNE product
- ModusToolbox™ Software
- PSOC™ Creator Software
- Radar Development Kit
- RUST
- USB Controllers SDK
- Wireless Connectivity Bluetooth Mesh Helper Applications
- XMC™ DAVE™ Software
- Überblick
- AIROC™ Bluetooth® Connect App Archive
- Cypress™ Programmer Archive
- EZ-PD™ CCGx Power Software Development Kit Archive
- ModusToolbox™ Software Archive
- PSOC™ Creator Archive
- PSOC™ Designer Archive
- PSOC™ Programmer Archive
- USB EZ-PD™ Configuration Utility Archives
- USB EZ-PD™ Host SDK Archives
- USB EZ-USB™ FX3 Archive
- USB EZ-USB™ HX3PD Configuration Utility Archive
- WICED™ Smart SDK Archive
- WICED™ Studio Archive
- Überblick
- Infineon Developer Center Launcher
- Infineon Register Viewer
- Pin and Code Wizard
- Timing Solutions
- Wireless Connectivity
- AKTUELLES IN
- Support
- Training
- Infineon Developer Community
- Neueste Nachrichten
Wirtschaftspresse
Dez. 16, 2025
Wirtschaftspresse
Dez. 11, 2025
Wirtschaftspresse
Dez. 08, 2025
Wirtschaftspresse
Dez. 04, 2025
- Unternehmen
- Unsere Geschichten
- Events
- Presse
- Investor
- Karriere
- Qualität
- Neueste Nachrichten
Wirtschaftspresse
Dez. 16, 2025
Wirtschaftspresse
Dez. 11, 2025
Wirtschaftspresse
Dez. 08, 2025
Wirtschaftspresse
Dez. 04, 2025



Cyberthreats are constantly evolving in order to take advantage of increased digitalization and connectivity. As governments, politicians, businesses and schools will come to rely on online connectivity and virtual communications tools they will be increasing their vulnerabilities and presenting more opportunities for cybercriminals to exploit.
Most of the consumers are left alone with evaluating security of devices, keeping security updated or changing passwords. And even businesses do not always have the know-how to evaluate security of tools they are using.
Defining minimum security requirements for connected devices is therefore a first and important step to increase cybersecurity. Considering security from the very beginning is key for digital products and business applications.
Secondly, cybersecurity should be as self-evident as safety. This can only be achieved through the definition of international standards, reliable testing and certification of products and the labelling of their security features.
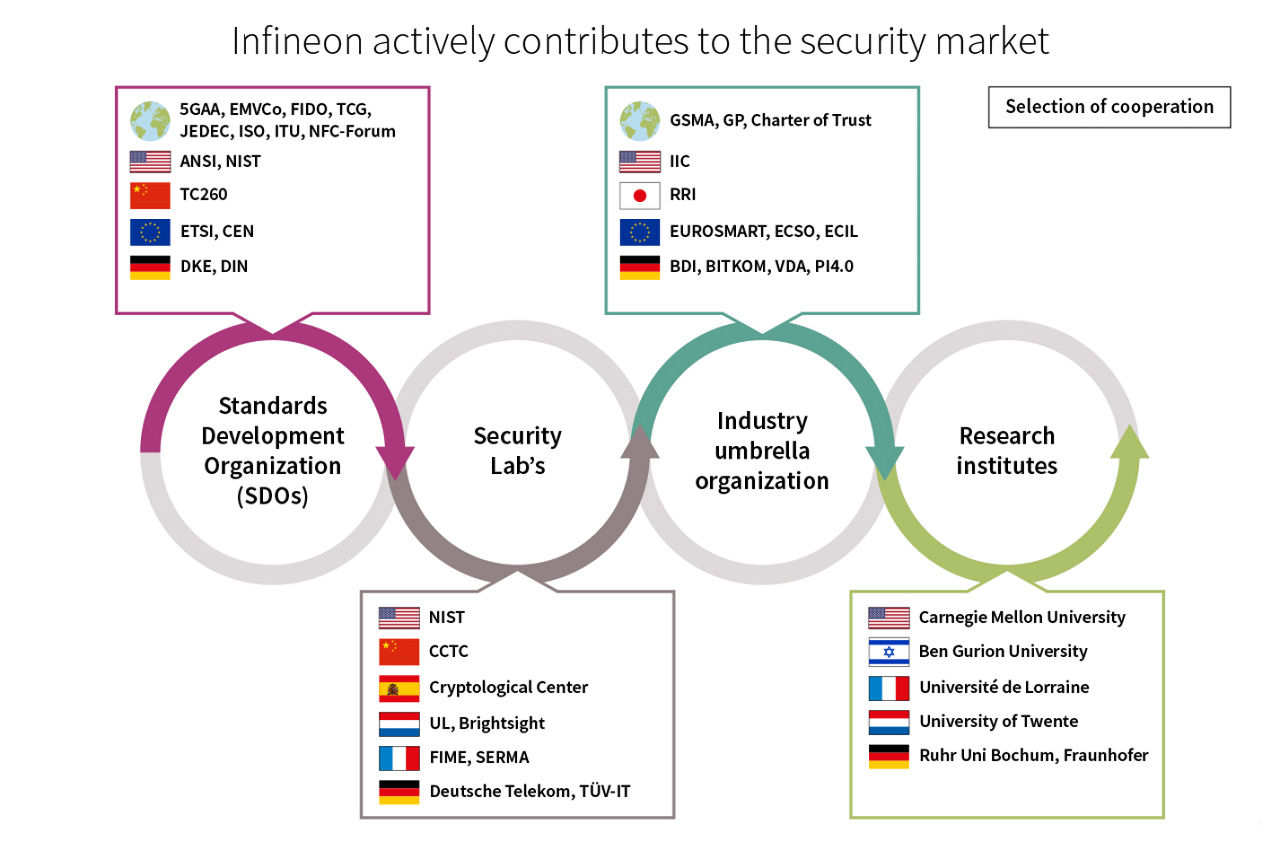
With its security expertise, system understanding and decades of experience in the security arena, Infineon is shaping the market through close cooperation with public authorities, as well as worldwide umbrella organizations focused on cybersecurity. As one of the first players in the electronics supply chain, Infineon provides the building blocks that will subsequently enable devices and services to be securely and reliably connected. Our state-of-the-art semiconductor technologies are already building a solid and trusted foundation for everything from connected cars through smart homes to automated factories.
Find out more about our product portfolio.





You would like to join lively discussion with cybersecurity experts? The Charter of Trust Geneva Online Roadshow is fully packed with interesting impulses
The virtual Geneva Roadshow will be introduced by Frankie Ng, CEO of SGS, who will underline the importance of the Charter of Trust and its raison d’être in an uncertain world. Florian Schütz, the Swiss Federal Cyber Security Delegate will hold a keynote speech on the Swiss Cybersecurity Strategy. Charter of Trust experts will focus on the Charter’s Principle 2 “Responsibility throughout the digital supply chain” and Principle 8 “Transparency and response”, highlighting how Charter of Trust members implement internal and external processes to strengthen cybersecurity.
The Charter of Trust is a global cybersecurity initiative aiming at building trust in the digital economy and improving safety in a hyperconnected world. Leveraging over 30 years of experience, Infineon is an active member of the Charter of Trust and helping to securely connect people, organizations and things.
The Internet of Things (ioT) connects the real with the digital world and is one of the most important technology trends of our time – as the number of devices within the IoT grows with each passing day, so too does the number of potentially accessible nodes. Hence protecting data and devices is vital in the face of a growing threat landscape.



What is the status of regulation, standardization & certfication of IT, ICT and IoT products and systems in the European Economic Area? What is the scope of the EU Cybersecurity Act? Which are the currently used security standards for CE products? Detlef Houdeau, Infineon’s security expert for public policy, gives a comprehensive overview of all existing and upcoming regulations, termini and standards with which device manufacturers should be familiar.
Take a look at the video on Regulation, Standardisation and Certification of IT, ICT and IoT products and systems in the EEA here.



The quantum computer enjoys the aura of a super computer that will shoot us into the next age of IT and is able to crack even the most robust of codes in a flash. Quantum-safe cryptography is often called post-quantum cryptography (PQC).
PQC comprises publickey encryption or digital signature algorithms that rely on the hardness of sophisticated mathematically problems. It is assumed that these problems are even intractable for powerful quantum and classical computers. To facilitate the development of new quantum-safe and practical schemes the National Institute of Standards and Technology (NIST) has started a standardization process.
Learn how standardization processes help preparing today for the potential danger of tomorrow here.



Securing your IoT solution/strategy is a vital necessity. Security must become a number one priority and be integrated from the beginning.
Building trust between IoT devices is the first step in a holistic strategy. IoT devices need strong, tamper-resistant protection. This degree of protection cannot be provided by software alone – it needs hardware-based security.
We recommend a security solution which is optimized for IoT devices and use cases and helps to overcome typical business and operational challenges. More insights are available here.
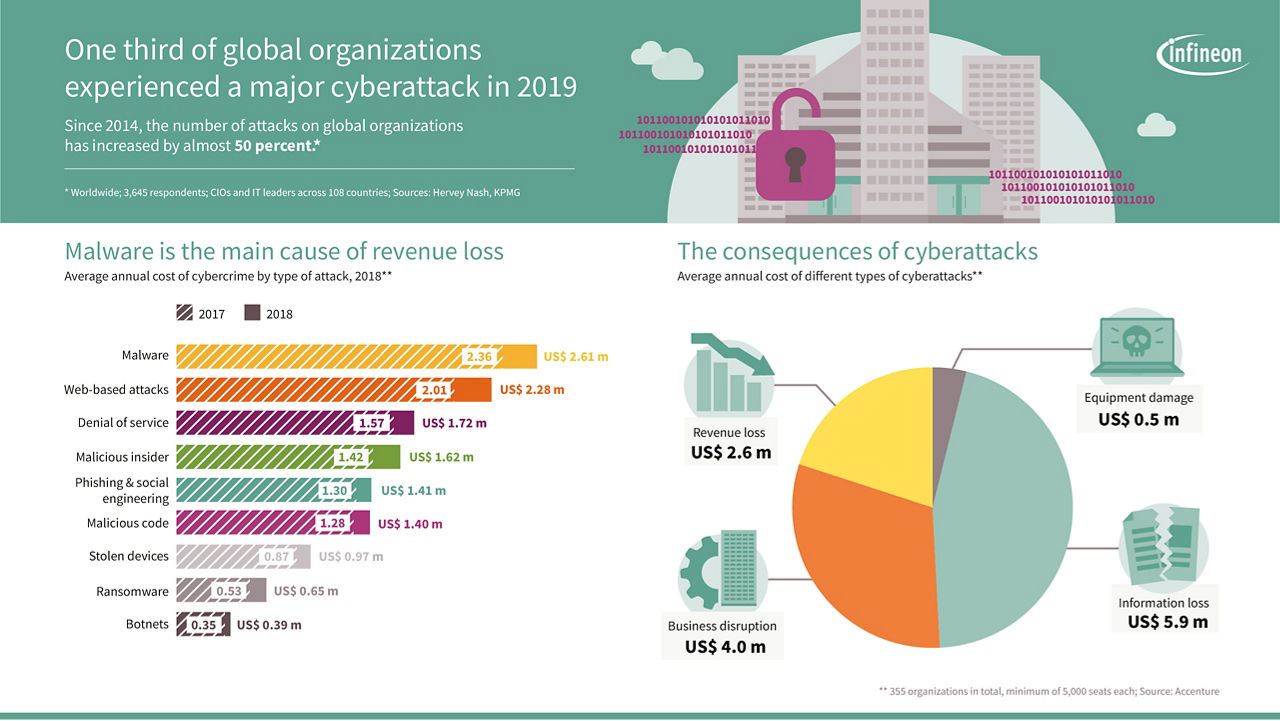
Since 2014, the number of attacks on global organizations has increased by almost 50 percent. By looking at the consequences of these cyberattacks, we can quickly realize that without security, digital technologies would not have broader acceptance for a longer period of time.
With the right level of security we can avoid information loss, business disruption and other grave impacts.


Downloads
Downloads



Cloud computing provides the tools and technologies to build data-intensive applications more affordable than traditional techniques. With millions of devices connected to the IoT, both manufacturers and consumers need to be sure that the identity of each and every device is genuine. Trusted device identities form the very basis for secured cloud connectivity and cloud computing. Therefore device identities need the best protection possible. Find out how Infineon improves cloud security.
In our fast moving world automation and interconnectivity are gathering pace. The entire value chain in the industry 4.0 is digitally connected, constantly supplying data and optimizing itself. Production is made faster, more efficient and more flexible. The urgency of Industrial Internet of Things (IIoT) security is becoming more and more apparent. It’s clear that security has come to the top of the agenda as a result of many high-profile cyberattacks.
Find out how Infineon enables the fourth industrial revolution.






Smart Home demands for intelligent devices that are equipped with sensors, controllers, actuators and security. This means they can collect, interpret and process data and then trigger appropriate actions or responses - all within a secured environment. Interoperability and communication between the devices and systems are prerequisites. Infineon is in the position to guide partners through this exciting new market while they can explore new opportunities and business models.
Cars are evolving fast. They are becoming digitized, connected and operate no longer as isolated vehicles. Already today, cars communicate with their environment, their passengers and with other vehicles. Connected cars bring a new level of convenience and excitement to drivers and passengers, but ‘being connected’ also allows the possibility of someone intruding your car. Connected cars can be vulnerable to malicious hacking, and security will be critical in the upcoming era of autonomous driving.
Find out how Infineon propels automotive data security to the next level.






The future of payment is contactless and mobile. We are on a journey towards seamless payment solutions that addresses consumers’ expectation of faster, easier and more convenient experiences. Already today almost anything can be turned into a contactless payment device. Consumers are able to carry payment accessories such as rings, bracelets or watches. This trend is paving the way for even more advanced IoT payment solutions. A connected fridge could detect that milk is missing, automatically order new one and pay for it. For all this security is a fundamental necessity.
Find out what Infineon offers for cashless payments.
Downloads
Downloads
The Internet of Things (ioT) connects the real with the digital world and is one of the most important technology trends of our time – as the number of devices within the IoT grows with each passing day, so too does the number of potentially accessible nodes. Hence protecting data and devices is vital in the face of a growing threat landscape.



What is the status of regulation, standardization & certfication of IT, ICT and IoT products and systems in the European Economic Area? What is the scope of the EU Cybersecurity Act? Which are the currently used security standards for CE products? Detlef Houdeau, Infineon’s security expert for public policy, gives a comprehensive overview of all existing and upcoming regulations, termini and standards with which device manufacturers should be familiar.
Take a look at the video on Regulation, Standardisation and Certification of IT, ICT and IoT products and systems in the EEA here.



The quantum computer enjoys the aura of a super computer that will shoot us into the next age of IT and is able to crack even the most robust of codes in a flash. Quantum-safe cryptography is often called post-quantum cryptography (PQC).
PQC comprises publickey encryption or digital signature algorithms that rely on the hardness of sophisticated mathematically problems. It is assumed that these problems are even intractable for powerful quantum and classical computers. To facilitate the development of new quantum-safe and practical schemes the National Institute of Standards and Technology (NIST) has started a standardization process.
Learn how standardization processes help preparing today for the potential danger of tomorrow here.



Securing your IoT solution/strategy is a vital necessity. Security must become a number one priority and be integrated from the beginning.
Building trust between IoT devices is the first step in a holistic strategy. IoT devices need strong, tamper-resistant protection. This degree of protection cannot be provided by software alone – it needs hardware-based security.
We recommend a security solution which is optimized for IoT devices and use cases and helps to overcome typical business and operational challenges. More insights are available here.
Since 2014, the number of attacks on global organizations has increased by almost 50 percent. By looking at the consequences of these cyberattacks, we can quickly realize that without security, digital technologies would not have broader acceptance for a longer period of time.
With the right level of security we can avoid information loss, business disruption and other grave impacts.



Downloads
Downloads



Cloud computing provides the tools and technologies to build data-intensive applications more affordable than traditional techniques. With millions of devices connected to the IoT, both manufacturers and consumers need to be sure that the identity of each and every device is genuine. Trusted device identities form the very basis for secured cloud connectivity and cloud computing. Therefore device identities need the best protection possible. Find out how Infineon improves cloud security.
In our fast moving world automation and interconnectivity are gathering pace. The entire value chain in the industry 4.0 is digitally connected, constantly supplying data and optimizing itself. Production is made faster, more efficient and more flexible. The urgency of Industrial Internet of Things (IIoT) security is becoming more and more apparent. It’s clear that security has come to the top of the agenda as a result of many high-profile cyberattacks.
Find out how Infineon enables the fourth industrial revolution.






Smart Home demands for intelligent devices that are equipped with sensors, controllers, actuators and security. This means they can collect, interpret and process data and then trigger appropriate actions or responses - all within a secured environment. Interoperability and communication between the devices and systems are prerequisites. Infineon is in the position to guide partners through this exciting new market while they can explore new opportunities and business models.
Cars are evolving fast. They are becoming digitized, connected and operate no longer as isolated vehicles. Already today, cars communicate with their environment, their passengers and with other vehicles. Connected cars bring a new level of convenience and excitement to drivers and passengers, but ‘being connected’ also allows the possibility of someone intruding your car. Connected cars can be vulnerable to malicious hacking, and security will be critical in the upcoming era of autonomous driving.
Find out how Infineon propels automotive data security to the next level.






The future of payment is contactless and mobile. We are on a journey towards seamless payment solutions that addresses consumers’ expectation of faster, easier and more convenient experiences. Already today almost anything can be turned into a contactless payment device. Consumers are able to carry payment accessories such as rings, bracelets or watches. This trend is paving the way for even more advanced IoT payment solutions. A connected fridge could detect that milk is missing, automatically order new one and pay for it. For all this security is a fundamental necessity.
Find out what Infineon offers for cashless payments.
