OPTIGA™ TPM - Trusted Platform Module
組み込みデバイス/組み込みシステムの完全性と信ぴょう性を保護
OPTIGA™ TPM(トラステッドプラットフォームモジュール)は標準化されたセキュリティコントローラを豊富に取り揃えており、組み込みデバイスや組み込みシステムの完全性と信ぴょう性を保護します。OPTIGA™ TPMセキュリティチップにはセキュアなキーストアが搭載され、各種暗号化アルゴリズムをサポートしているため、豊富な機能を駆使して重要なデータやプロセスを確実に保護します。
OPTIGA™ TPMセキュリティコントローラは、WindowsやLinux(およびその派生OS)が稼働するプラットフォームに最適です。こうしたプラットフォームでは、 トラステッドコンピューティンググループ(TCG)標準に基づいてTPM 1.2、または最新のTPM 2.0標準をサポートしています。
System health check for network equipment and IoT devices
Today, network equipment and IoT devices face a constant barrage of attacks aimed at exposing vulnerabilities in software and firmware. Worst still, cyber threats have become so sophisticated that conventional defense-in-depth cybersecurity measures may even fail to detect them. Once malware is on a device, it may remain there undetected for long periods as it often works undetected in the background. By the time most users realize they have suffered a data breach, they have actually been under attack for weeks, months, or even years.
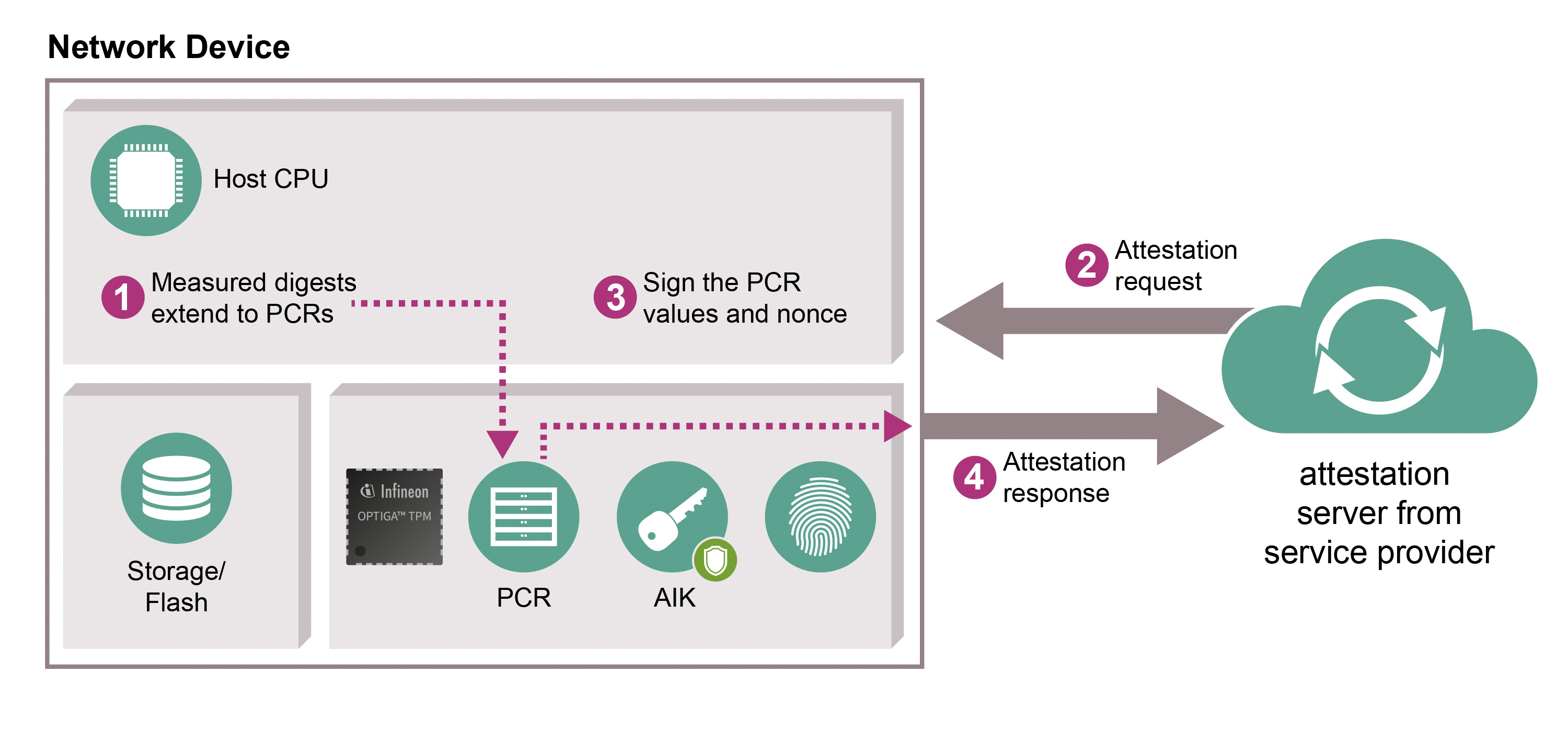
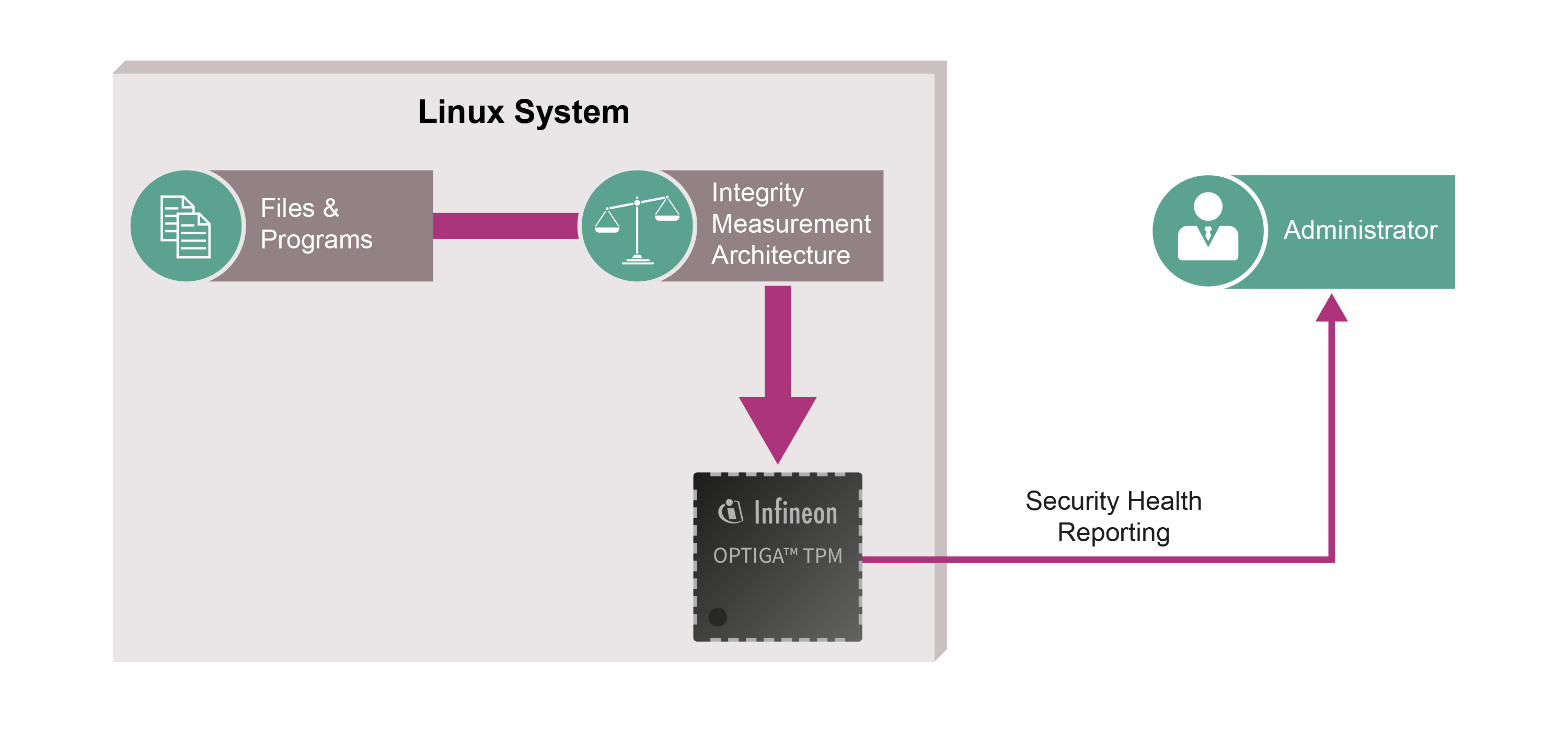
A system health check supported by Infineon’s OPTIGATM TPM lets users check that their devices have not been manipulated. The TPM provides a secured identity and storage space for system control mechanisms that may check whether hardware and software are still running as intended. The system notifies the user if it does detect changes, e.g. caused by malware.
When devices start up, the software and firmware are measured by the Linux Integrity Measurement Architecture (IMA) and the results are stored in the OPTIGATM TPM Platform Configuration Registers (PCRs). The measurements can then be retrieved by a remote attestation server to determine the configuration of the device at the time it was booted as well as during runtime. The PCR is protected against being rolled back to a previous value. The attestation server polls a platform at set intervals, verifying either that the PCRs in the OPTIGATM TPM have not changed or that the new PCR values are trustworthy. The PCR values are signed with a private Attestation Identity Key (AIK) to reduce the risk of forgery.
For service providers, this means that their services are stable and reliable, and that devices in their network have been checked for manipulation. OPTIGATM TPM also gives device and system manufacturers an opportunity to access new markets requiring new – and differentiating – levels of security. End users benefit from increased security for their sensitive data while still enjoying the same or an even better user experience.
To facilitate use and integration for device and system manufacturers, Infineon has created a Github repository with documents as well as demonstrator source code.
A system health check supported by Infineon’s OPTIGA™ TPM - Video
セキュリティに対する高まる要求を満たすため、メーカーとシステムプロバイダーの多くは既存あるいは新規のコンピュータ設計にシームレスに組み入れ、迅速な設計と配置をサポートするカスタム化された実装が容易なソリューションを探しています。トラステッドコンピューティンググループ(TCG)は、相互運用性のあるトラステッドコンピューティングプラットフォームをサポートするため、一連のオープンでベンダー中立の世界標準業界規格を定義しました。トラステッドコンピューティングはコンピュータデバイス内蔵の実証済みセキュリティアンカーによってシステムへの許可されない変更を検出することを狙いとしています。この機能は、暗号キーのデバイスへのセキュアな統合をサポートする専用マイクロプロセッサにより実現されます。トラステッドプラットフォームモジュール(TPM)に保管された基本キーは内部で処理されて使用され、このモジュールではすべての暗号機能が保護されます。コンピュータ設計で長年の使用実績があることから、今やトラステッドコンピューティングは自動車や産業オートメーションに至るまでのさまざまな分野で、アプリケーションの範囲を大きく広げることになりました。
TCGの創立メンバーの一員であり、またTCG主要活動メンバーであるインフィニオンはお客様に対して標準化の利点を提供し続けています。インフィニオンの目的はお客様が統合にかける労力を軽減し、強力で実証されたセキュリティソリューションを可能にすることです。インフィニオンが長年にわたり蓄積した専門知識と信頼を基礎に、お客様は秘密データの保護、強固なマシン識別と安全性の確立、証明書、キー、パスワードの保護によるセキュアな認証サポートができます。インフィニオンのグローバルサポートチームによって、インフィニオンは広い温度範囲と標準インターフェイスをサポートするOPTIGA™ TPM製品を提供します。実際インフィニオンのTPM1.2製品にTPM2.0を補完することにより、インフィニオンは次世代の組込みトラステッドコンピューティングアプリケーションをサポートする最初の半導体メーカーとなりました。 OPTIGA™ TPMファミリーおよびインフィニオンのポートフォリオが個々のアプリケーションに合わせたさまざまなインターフェイス、パッケージ温度範囲にどのようにスケーリングするかをご確認ください。
- 標準化による統合の簡易化、信頼性、ソフトウェア再利用性の利点
- 優れたサポートと広範囲の革新的な認証済み製品
- 業界初のTPM2.0製品によりTPM1.2から2.0への円滑な移行

The IoT Solutions World Congress awarded Infineon for Best Solution in Manufacturing. Mocana, who recently joined the Infineon Security Partner Network (ISPN) and Infineon take security for IoT to the next level by combining advanced security features with our highly valued and widely used OPTIGA™ TPM.
Ecosystem and ISPN partner support of OPTIGA™ TPM

With more than 15 years of experience in designing TPM-based solutions and more than 20 scientific publications, the Fraunhofer Institute for Secure Information Technology (SIT) is one of the leading experts in the field of Trusted Computing. Fraunhofer SIT's involvement ranges from the standardization body over practical implementations to fundamental research. Fraunhofer SIT is involved throughout all application sectors, from desktop and server equipment, over automotive and railway to industrial applications.
Fraunhofer SIT's offers include:
*application sector specific design and architectures for TPM-based security solutions
*consultancy, teaching and empowerment on TPM integration
*extension and customizations of the Open Source Software Stack

GlobalSign provides PKI-based device identity enrollment and management solutions that leverage Infineon products such as the OPTIGA™ TPM SLM 9670 and SLB 9670 as the trust anchor. GlobalSign´s security products are targeted towards various IIoT verticals, including but not limited to - smart manufacturing, automotive, industrial automation and healthcare. GlobalSign brings experience and expertise in using PKI and SSL technologies and applying them towards solving cybersecurity problems in various small and large business contexts through their comprehensive product portfolio.
GlobalSign IoT Identity Platform can create and host custom PKI hierarchies that serve the core identity needs of devices embedded with Infineon OPTIGA™ TPMs.
GlobalSign IoT Edge Enroll is an endpoint software application that can provide device registration, enrollment and provisioning services. More information

Sectigo provides a complete certificate management solution starting with secure certificate creation & insertion at the customer´s factory using the OPTIGA™ TPM for private key storage. The Floodgate Factory CA Server enables key management and certificate signing during manufacturing. The Floodgate TPM Library provides the device-side software to streamline TPM usage and key storage, while the Floodgate CA Server allows management of PKI certificates after the device is deployed.Floodgate TPM Library and the Floodgate PKI Client enable OEMs to develop and deploy secure embedded connected devices with relative ease.
Together, Sectigo and Infineon provide:
- the APIs, libraries, and code running on the device to enable integration with the OPTIGA™ TPM
- key generation by the OPTIGA™ TPM and enrollment with Certificate Authority
- Certificate Signing Requests using the Simple Certificate Enrollment Protocol (SCEP), Enrollment over Secure Transport (EST), and Online Certificate Status Protocol (OCSP)
- Full integration with public and private Certificate Authorities

With about 15 years of experience in different security related projects and applications, Mixed Mode is a knowledgeable Infineon partner offering consulting services and software development for integration of the OPTIGA™ TPM. Amongst different projects, Mixed Mode developed and implemented a secure boot and secure update concept including hardware integration as well as verification of the LINUX image.
Mixed Mode has experience on different target embedded platforms, operating systems and use cases secured by OPTIGA™ TPM:
- Supported platforms: LINUX, RTOS, Bare Metal
- Supported use cases: Secure Communication, Secure Storage, Secure Boot, Secure Update
- Consulting services: Training, Workshops, Security Concepts / Security by Design, Code and Gap Analysis, ISO 62443 SL 3, Policy and Certificate Concepts
- Others: DRM (Digital Rights Management) and License Management on Embedded Platforms

wolfTPM is a TPM 2.0 project, designed for embedded use. It is highly portable, due to having been written in native C, having a single IO callback for SPI hardware interface, no external dependencies, and its compacted code with low resource usage.
It is generally very easy to compile on new platforms, so if your desired platform is not listed as supported or you would like assistance porting wolfTPM, please contact wolfSSL at facts@wolfssl.com.
Features:
*Provides all TPM 2.0 API's in compliance with the specification.
*Uses the TPM Interface Specification (TIS) to communicate over SPI.
*Includes wrappers for Key Generation, RSA encrypt/decrypt, ECC sign/verify, ECDH, NV Access and Hashing.