Embedded security for the Internet of Things (IoT)
Please choose a subcategory
Protect consumers and businesses – with the right security
From remotely checking in on a smart factory, to conveniently working from home, to relaxing in a driverless car, the Internet of Things (IoT) is paving the way for many exciting new opportunities. For businesses, IoT means new enterprises, new business models and new revenue streams. But the inherent nature of IoT – connecting ‘things’ to each other and to the cloud to form a network – gives rise to a host of new security threats. That’s why the right security must be an integral part of each IoT design.
The right security – the basis for IoT
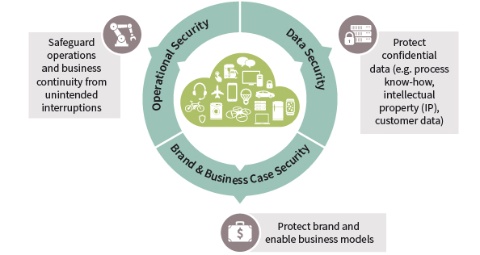
Equipping smart devices, connected cars, companies and Industry 4.0 factories with the right security solutions from the get-go is key to helping prevent attacks – whether theft, fraud or manipulation. The right security helps to protect a company’s IP and data, and to maintain customer confidence in its brand and products. Further, the right security solutions for IoT can help a company:
- Enable new business models
- Differentiate and grow
- Save costs
Why hardware security is a must
Companies who are looking for a security solution need one that is equally easy to use – in terms of fast integration and time to market – and trustworthy. Unlike software-only solutions a hardware-based solution is strong, tamperproof and provides a solid foundation. In addition Infineon´s independently-certified hardware security solutions are pre-integrated and therefore easy to integrate into your system.
Your partner for IoT security
With Infineon’s market leading expertise and wide range of cutting-edge products and solutions, you gain an outstanding partner to guide you through the increasingly complex security solutions landscape. Our experts can help reduce your security system’s complexity so you can bring a product to market more quickly. We can flexibly scale our broad selection of semiconductors for hardware-based security across all platforms.
By using IoT security solutions from Infineon you also benefit from:
- A competitive edge thanks to top-of-the-line security
- Reduced time-to-market with easily integrated solutions and outstanding support
- A security solution tailored to IoT application needs
Turn to Infineon for peace of mind that your project will have the right level of security – with minimal effort on your part. You also benefit from excellent support, which many customers tell us is second to none.
Explore our IoT security solutions now to find the right security for your design.
Infineon is the recipient of “IT Security Made in Germany” seal









