OPTIGA™ TPM - Trusted Platform Module
Security controllers based on TCG specifications (TPM 1.2 or TPM 2.0) protecting integrity and authenticity of embedded devices and systems
OPTIGA™ TPM (Trusted Platform Module) offers a broad portfolio of standardized security controllers to protect the integrity and authenticity of embedded devices and systems. With a secured key store and support for a variety of encryption algorithms, OPTIGA™ TPM security chips provide robust protection for critical data and processes through their rich functionality.
OPTIGA™ TPM security controllers are ideal for platforms running both Windows and Linux and its derivatives (SLB 9645 product versions for Chrome OS available). Based on Trusted Computing Group (TCG) standards, they support the TPM 1.2 or the latest innovative TPM 2.0 standard.

Infineon Developer Community is available 24x7 for you to connect and network with engineers across the globe. Get help from Infineon support engineers, and expert members to solve your design challenges anytime, from anywhere, in any topic, and in your preferred language.
System health check for network equipment and IoT devices
Today, network equipment and IoT devices face a constant barrage of attacks aimed at exposing vulnerabilities in software and firmware. Worst still, cyber threats have become so sophisticated that conventional defense-in-depth cybersecurity measures may even fail to detect them. Once malware is on a device, it may remain there undetected for long periods as it often works undetected in the background. By the time most users realize they have suffered a data breach, they have actually been under attack for weeks, months, or even years.
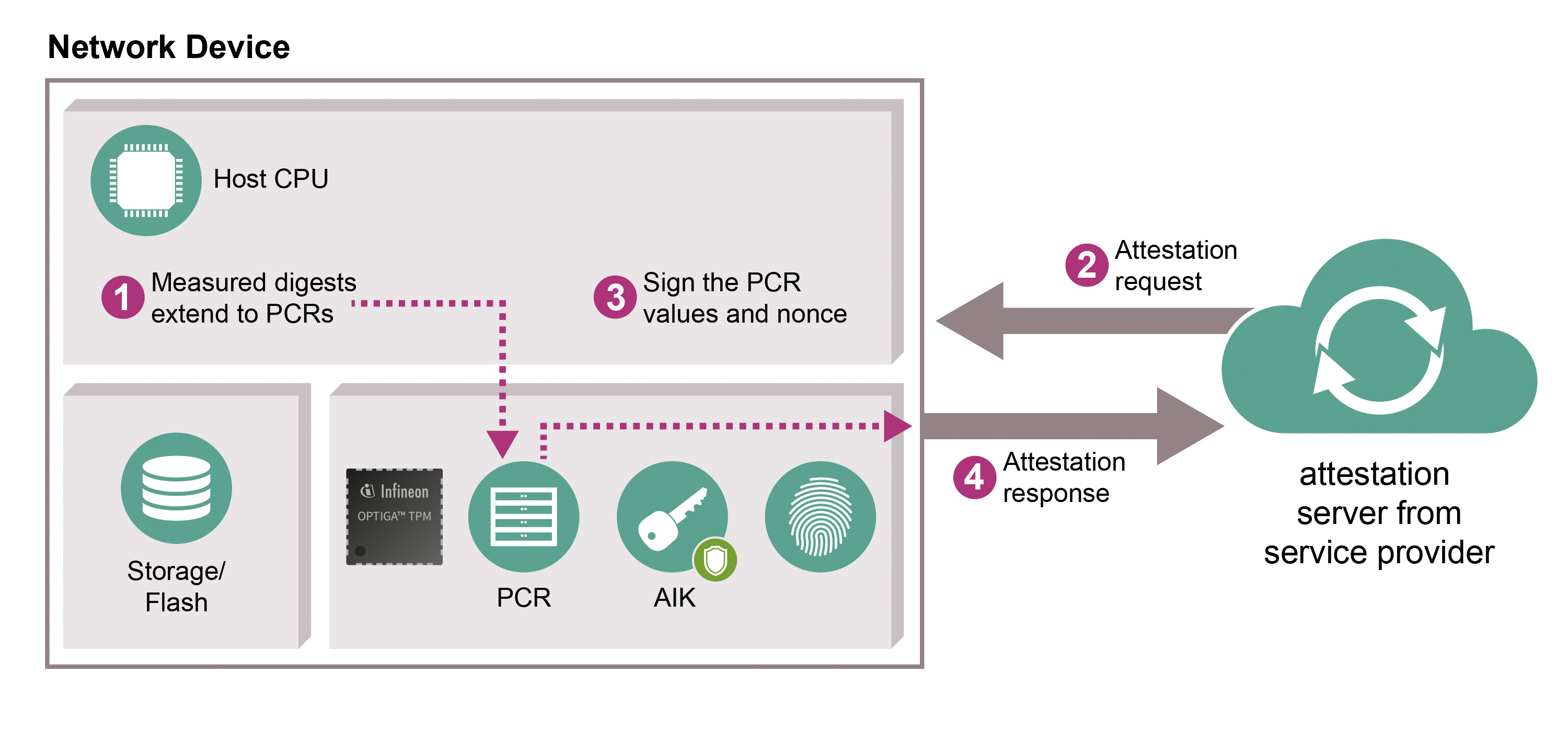
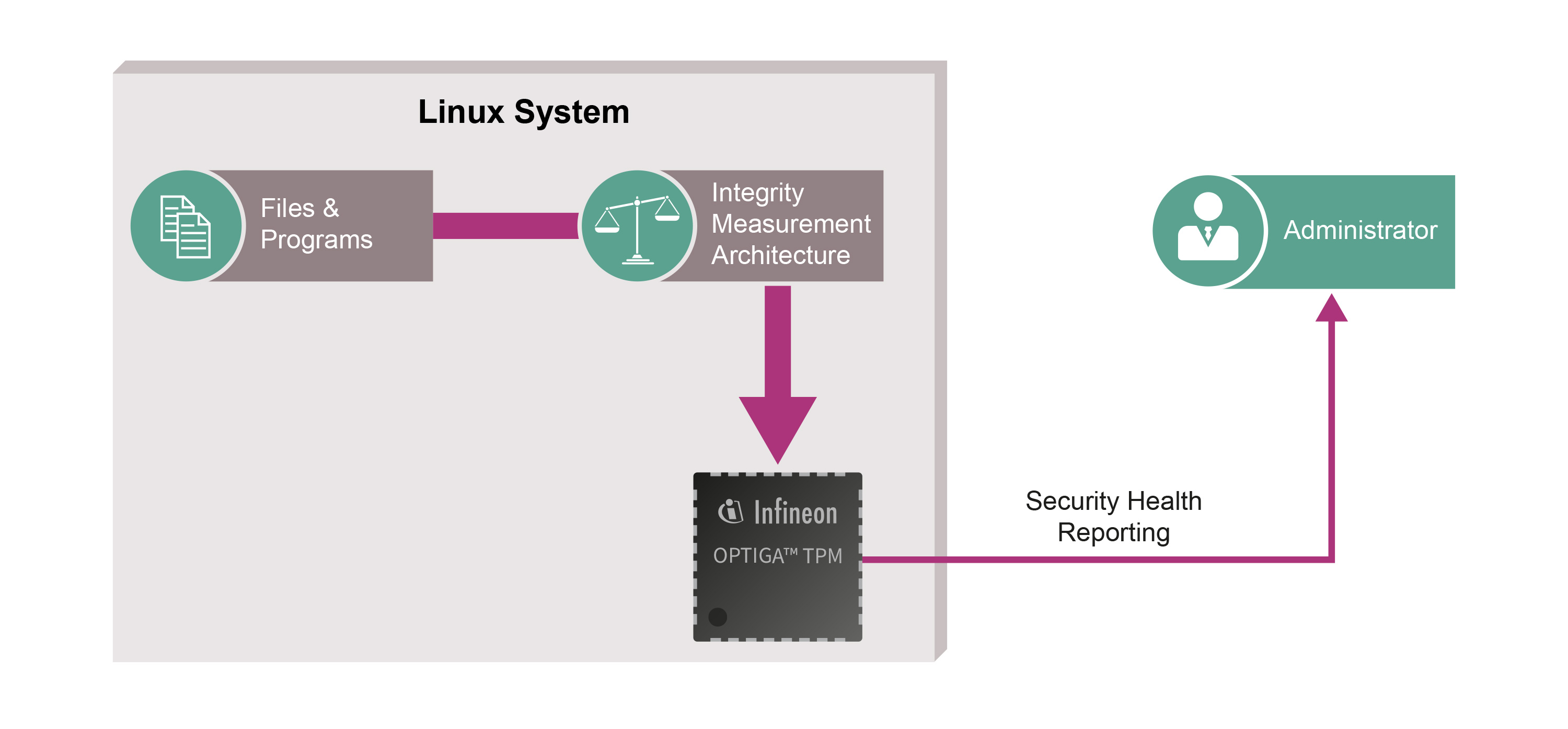
A system health check supported by Infineon’s OPTIGATM TPM lets users check that their devices have not been manipulated. The TPM provides a secured identity and storage space for system control mechanisms that may check whether hardware and software are still running as intended. The system notifies the user if it does detect changes, e.g. caused by malware.
When devices start up, the software and firmware are measured by the Linux Integrity Measurement Architecture (IMA) and the results are stored in the OPTIGATM TPM Platform Configuration Registers (PCRs). The measurements can then be retrieved by a remote attestation server to determine the configuration of the device at the time it was booted as well as during runtime. The PCR is protected against being rolled back to a previous value. The attestation server polls a platform at set intervals, verifying either that the PCRs in the OPTIGATM TPM have not changed or that the new PCR values are trustworthy. The PCR values are signed with a private Attestation Identity Key (AIK) to reduce the risk of forgery.
For service providers, this means that their services are stable and reliable, and that devices in their network have been checked for manipulation. OPTIGATM TPM also gives device and system manufacturers an opportunity to access new markets requiring new – and differentiating – levels of security. End users benefit from increased security for their sensitive data while still enjoying the same or an even better user experience.
To facilitate use and integration for device and system manufacturers, Infineon has created a Github repository with documents as well as demonstrator source code.
Remote device health attestation supported by Infineon´s OPTIGA™ TPM – watch the video now
Glossary
- High-end security controller with advanced cryptographic algorithms implemented in hardware (e.g. RSA & ECC256, SHA-256)
- Common Criteria (EAL4+) and FIPS security certification
- Flexible integration thanks to SPI, I2C or LPC interface support
- Extended temperature range (-40 to +85°C) for a variety of applications
- Reduced risk based on proven technology
- Fast time to market through concept reuse
- Easy integration into all platform architectures and operating systems (Windows, Linux & derivatives
In a bid to meet rising demand for security, many manufacturers and system providers are looking for customized, easy-to-implement solutions that support rapid design-in and deployment by integrating seamlessly into existing and new computing designs. The Trusted Computing Group (TCG) has defined a range of open, vendor-neutral, global industry standards to support interoperable, Trusted Computing platforms. Trusted Computing aims to detect unauthorized changes to a system based on an established security anchor embedded in a computing device. This is achieved with a dedicated microprocessor to support the secured integration of cryptographic keys into the device. The basic keys stored in the Trusted Platform Module (TPM) are processed and used internally, with all cryptographic functions being protected. Long established in computer designs, Trusted Computing is now moving into a much broader application spectrum across industries as diverse as automotive and industrial automation.
As one of the founding members and key drivers within TCG, Infineon continues to bring the benefits of standardization to its customers. Our aim is to provide you with strong, proven security solutions offering reduced integration effort. You can build on our long-standing expertise and reliability to protect sensitive data, establish strong machine identity and integrity, and support secure authentication by protecting certificates, keys and passwords. Backed by our global support team, we offer a market-leading range of OPTIGA™ TPM products supporting all standard interfaces over a wide temperature range. In fact, we were the first semiconductor player to complement our TPM 1.2 offering with a TPM 2.0 product to support the next generation of embedded Trusted Computing applications. Find out more about our OPTIGA™ TPM family and how our portfolio scales across interfaces, packages and temperature ranges to meet individual application needs.

The IoT Solutions World Congress awarded Infineon for Best Solution in Manufacturing. Mocana, who recently joined the Infineon Security Partner Network (ISPN) and Infineon take security for IoT to the next level by combining advanced security features with our highly valued and widely used OPTIGA™ TPM.
Ecosystem and ISPN partner support of OPTIGA™ TPM

With more than 15 years of experience in designing TPM-based solutions and more than 20 scientific publications, the Fraunhofer Institute for Secure Information Technology (SIT) is one of the leading experts in the field of Trusted Computing. Fraunhofer SIT's involvement ranges from the standardization body over practical implementations to fundamental research. Fraunhofer SIT is involved throughout all application sectors, from desktop and server equipment, over automotive and railway to industrial applications.
Fraunhofer SIT's offers include:
*application sector specific design and architectures for TPM-based security solutions
*consultancy, teaching and empowerment on TPM integration
*extension and customizations of the Open Source Software Stack

GlobalSign provides PKI-based device identity enrollment and management solutions that leverage Infineon products such as the OPTIGA™ TPM SLM 9670 and SLB 9670 as the trust anchor. GlobalSign´s security products are targeted towards various IIoT verticals, including but not limited to - smart manufacturing, automotive, industrial automation and healthcare. GlobalSign brings experience and expertise in using PKI and SSL technologies and applying them towards solving cybersecurity problems in various small and large business contexts through their comprehensive product portfolio.
GlobalSign IoT Identity Platform can create and host custom PKI hierarchies that serve the core identity needs of devices embedded with Infineon OPTIGA™ TPMs.
GlobalSign IoT Edge Enroll is an endpoint software application that can provide device registration, enrollment and provisioning services. More information

Sectigo provides a complete certificate management solution starting with secure certificate creation & insertion at the customer´s factory using the OPTIGA™ TPM for private key storage. The Floodgate Factory CA Server enables key management and certificate signing during manufacturing. The Floodgate TPM Library provides the device-side software to streamline TPM usage and key storage, while the Floodgate CA Server allows management of PKI certificates after the device is deployed.Floodgate TPM Library and the Floodgate PKI Client enable OEMs to develop and deploy secure embedded connected devices with relative ease.
Together, Sectigo and Infineon provide:
- the APIs, libraries, and code running on the device to enable integration with the OPTIGA™ TPM
- key generation by the OPTIGA™ TPM and enrollment with Certificate Authority
- Certificate Signing Requests using the Simple Certificate Enrollment Protocol (SCEP), Enrollment over Secure Transport (EST), and Online Certificate Status Protocol (OCSP)
- Full integration with public and private Certificate Authorities

With about 15 years of experience in different security related projects and applications, Mixed Mode is a knowledgeable Infineon partner offering consulting services and software development for integration of the OPTIGA™ TPM. Amongst different projects, Mixed Mode developed and implemented a secure boot and secure update concept including hardware integration as well as verification of the LINUX image.
Mixed Mode has experience on different target embedded platforms, operating systems and use cases secured by OPTIGA™ TPM:
- Supported platforms: LINUX, RTOS, Bare Metal
- Supported use cases: Secure Communication, Secure Storage, Secure Boot, Secure Update
- Consulting services: Training, Workshops, Security Concepts / Security by Design, Code and Gap Analysis, ISO 62443 SL 3, Policy and Certificate Concepts
- Others: DRM (Digital Rights Management) and License Management on Embedded Platforms

wolfTPM is a TPM 2.0 project, designed for embedded use. It is highly portable, due to having been written in native C, having a single IO callback for SPI hardware interface, no external dependencies, and its compacted code with low resource usage.
It is generally very easy to compile on new platforms, so if your desired platform is not listed as supported or you would like assistance porting wolfTPM, please contact wolfSSL at facts@wolfssl.com.
Features:
*Provides all TPM 2.0 API's in compliance with the specification.
*Uses the TPM Interface Specification (TIS) to communicate over SPI.
*Includes wrappers for Key Generation, RSA encrypt/decrypt, ECC sign/verify, ECDH, NV Access and Hashing.
| OPTIGA™ Trusted Platform Module & AURIX™: Perfect partners for automotive cybersecurity |
|