Automotive security
Please choose a subcategory
Infineon enables automotive security systems
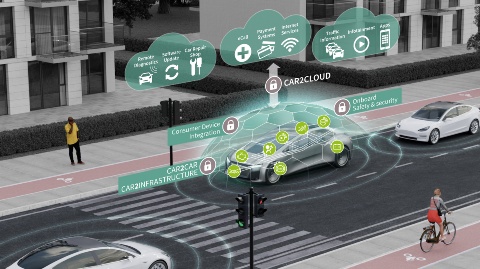
As system complexity increases in cars, so too does the volume of data to be processed and distributed. New payment methods, such as parking fees or road tolls, require a secure flow of transaction data. Infineon can draw on years of expertise in chip card and identification systems to propel automotive data security to the next level.
Where there is light, there is also darkness. The accessibility of a vehicle from outside also significantly increases the risk of hacker attacks. Outside attacks (e.g. via mobile phone, Bluetooth or Wi-Fi) have been discussed and explained in numerous publications. Automakers therefore need to ensure that information is processed securely and protected against external access and manipulation (e.g. car tuning or counterfeit spare parts). Infineon’s semiconductor solutions enable the installation of automotive security systems. These kinds of security systems protect fair competition in the global market, assets, personal data and, last but not least, the lives and limbs of the users on the road.
Infineon’s product development process now certified to ISO/SAE 21434

Infineon is the industry’s trusted partner for automotive security. TÜV Nord has now certified Infineon’s company-wide product development process according to ISO/SAE 21434. The company-wide certification includes:
- Cybersecurity management
- Continuous cybersecurity activities (e.g. monitoring, risk assessment, vulnerability analysis)
- Risk assessment methods (e.g. threat identification)
- Concept phase (e.g. cybersecurity goals)
- Product development phase (e.g. integration and verification)
- Post development phase (e.g. cybersecurity incident response)
In addition, Infineon's AURIX™ TC4x microcontroller family features an innovative cybersecurity cluster. TC4x meets the new ISO 21434 security standard and enables your system to meet UNECE WP.29.
Explore our interactive graphic and learn more about our automotive security portfolio
We have the right level of security
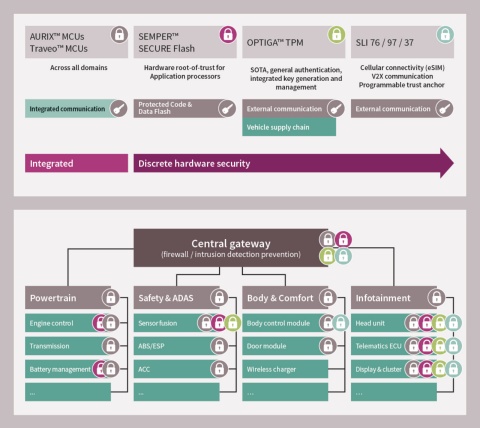
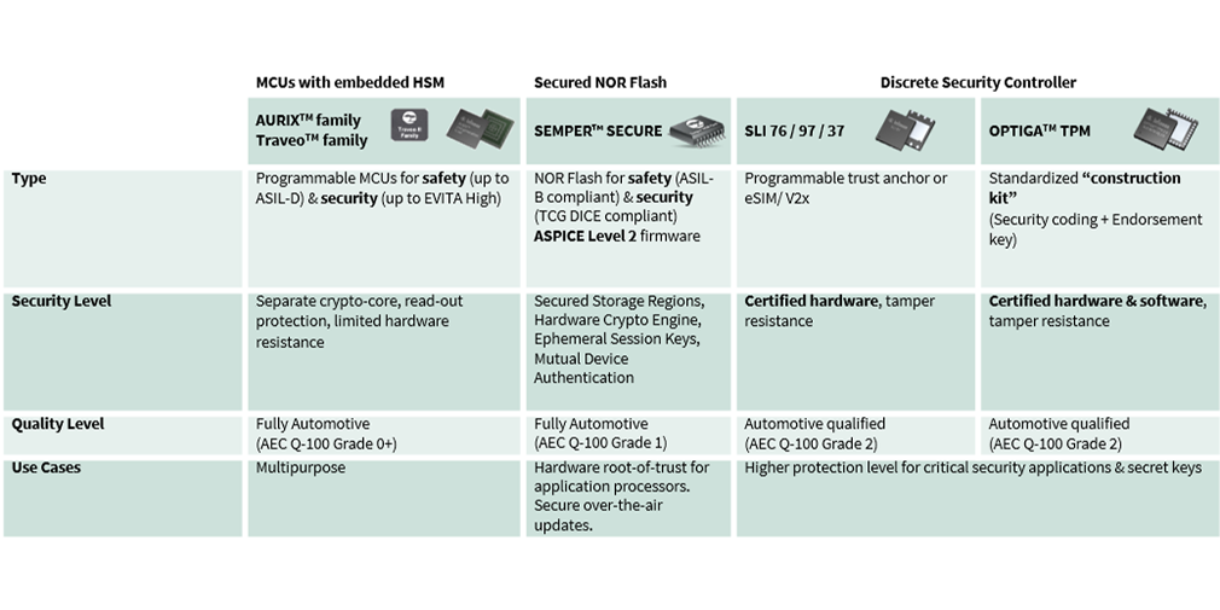
As the global market leader in security microcontrollers for 15 consecutive years and with more than 40 years of experience in the automotive sector, Infineon offers a broad portfolio of cost-effective automotive security solutions. The product range includes hardware components, such as 32-bit microcontrollers with embedded hardware security modules, SIM cards, and secure elements as well as related software packages. This permits the security level and, consequently, the associated cost to be customized precisely to the protection needs of a particular application. Customers benefit from decades of experience in the analysis of threat and attack scenarios by virtue of security certifications, for instance the ISO/IEC 15408 (Common Criteria), and the extensive portfolio of hard- and software patents. Here Infineon consistently relies on proven industry standards, such as AES-128, ECC-256, SHE, EVITA HSM and TPM, to lower the integration effort as well as the risk of OEMs and their tier suppliers.

Description:
- Get to know why systems require frequent updates, how this is done and how automotive systems try to ensure their security when they are updated
- Learn how AURIX™ families of microcontrollers support over-the-air software updates

Description:
- Understand how hackers use the CAN bus to interfere with in-vehicle communication
- Be aware of how Infineon’s AURIX™ microcontrollers support secure CAN communication

Description:
- Be aware of the growing market for connected cars
- Recognize how connectivity poses a challenge to security
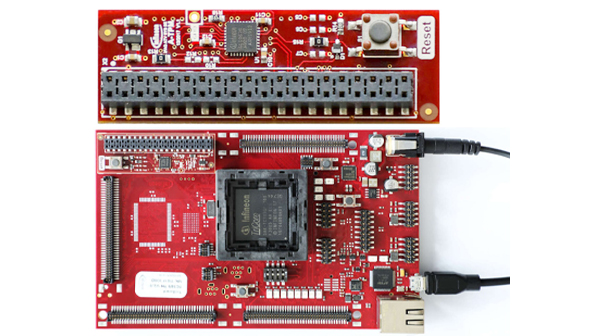
- Understand how the 1st Generation AURIX™ Hardware Security Module (HSM) works, its key features and applications

Description:
- Identify common security threats to modern cars
- Understand how OPTIGA™ TPM can help automotive systems achieve a high level of security and their applications in different use cases in various host environments

Description:
- Indicate the trends, market segments and Infineon products aimed at each segment
- Identify the major players and Infineon’s main strengths in relation to each competitors.

Description:
- Find out about the definition of gateway and zone controllers and their typical applications.
- Discover the new routing requirements in gateway and zone controllers, and get an overview of the most generic block diagrams for gateway and zone controller units.

Description:
- Categorize cybersecurity threats in the upcoming automotive electrical and electronic architecture
- Identify how Infineon’s next-generation AURIX™ TC4x microcontrollers are able to mitigate cybersecurity threats
By the end of this training, you will be able to
- Describe the main features of Infineon’s TRAVEO™ T2G microcontrollers
- Recognize the different variants that make up this family of products