
Enable smart mobility with Infineon’s comprehensive system understanding and proven security solutions today and tomorrow. For a long time the concept of car safety was synonymous with seatbelts, an adequately sized crumple zone, and airbags. Devices such as these protect drivers and passengers from physical dangers caused by accidents. But in the age of the connected car, safety functionality may also be impacted negatively by humans deliberately deploying cyber- attacks on the car similar to those seen on the internet for some time. Therefore cyber-security in the car becomes a priority.
Where do I need car security in my daily car usage?

Solutions
Connected car
The connected car is key to the future of motoring. Cars will be able to have full internet access, use mesh communications to other vehicles and interact with road infrastructure on local traffic conditions.
Connectivity of the car to outside entities is fostering new business model and related services will be major differentiators for the car manufacturers. Technologies – such as car-to-car communication and autonomous cars - that would have seemed utopian until recently are on the verge of becoming a reality. However, this increased level of communication also opens up the risk for cyber-attacks. Therefore car security is becoming an increasingly important topic.
According to Prof. Christof Paar, Chair for Embedded Security at Ruhr-Universität Bochum, vehicle electronics require strong security protection that is supported both by software and hardware to reduce risk of damage from cyber-attacks. Such hardware-based security components are widely viewed as a prerequisite to enable manufacturers to build consumer trust in the security of new vehicle technologies and their applications.
Partner
Infineon - your partner for car security
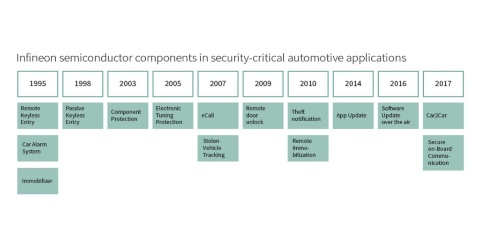
Our experts have been developing semiconductor solutions for the automotive industry for decades. Their colleagues from the Connected Secure Systems division have been developing security ICs for over a quarter of a century that today used in many security sensitive applications like laptops and electronic passports. We have pooled this expertise and can offer our customers scalable security solutions, as we integrate our diverse product range with in-depth system knowledge.
Cyber security in vehicles
Cyber-security within a car means that vehicle systems are protected against manipulation and that their error-free function is ensured. At the same time, communication within the vehicle, between vehicles, and with the rest of the world (e.g. via the internet) needs to be secure. Secret keys and encryption algorithms are efficient means of securing communication channels. However, to fully shield these channels from tampering and also to provide the processing speed needed for real-time encryption and decryption, electronic solutions such as secure elements and microcontrollers with built-in security modules are required. These measures effectively prevent theft, forgery and tampering.
Protection against financial losses
Chip tuning, odometer tampering, counterfeit substitution can happen on electronic component, and sub-assembly level because of poor car security and impose a substantial financial risk for the OEM and the car owners: According to studies by Germany’s ADAC automobile association, every year in Germany the many thousands of tampered odometers mislead buyers to a car’s real value, costing them billions of euros . Also, numerous reports have revealed that the market for stolen luxury vehicles continues to grow.
Safety and security
In the connected car, the electronics play an essential role to increase safety on the road. Potential or actual failures of crucial safety components such as brakes and airbags must be notified and even autonomously acted on, in order to keep the vehicle and its passengers safe from harm. At the same time, cyber-security is becoming more and more important. The higher level of vehicle communication with the outside world also increases the risk of electronic control units such as used in the engine, brakes, or steering being tampered with. For this reason, the data integrity of all safety-critical functions needs to be protected.
Microcontrollers with dedicated security functions
Microcontrollers (MCUs) are a key element in electronic systems, as they are able to control processes and handle monitoring and security tasks. In safety-related systems such as those encountered in cars, MCUs must not only meet safety requirements but also support security protocols. In this context, MCUs that already support the required security functions in hardware are a very good solution. Infineon’s AURIX™ microcontrollers feature a built-in hardware security module (HSM) to protect software and data communication within the vehicle. They thus provide effective protection against hackers wanting to infiltrate the on-board systems.
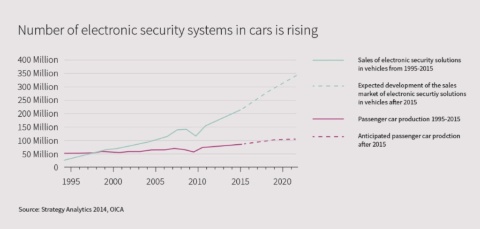
Increase in electronic security systems
An increasing number of new vehicles are leaving factories with pre-installed electronic car security systems. Experts anticipate that this number will even double in the coming years.
Further information
Last update: October 2016


